Difference between revisions of "KHIKA App for Fortigate Firewall"
(→Some suggestions for useful interaction with this dashboard could be :) |
(→Alerts Description) |
||
| Line 292: | Line 292: | ||
|- | |- | ||
|Fortigate firewall successful sweep scan activity by malicious ip | |Fortigate firewall successful sweep scan activity by malicious ip | ||
| − | | | + | |This alert is triggered when more than 10 connections happened from same malicious IP and status is deny followed by a successful login status using different Destination IP, within one minute |
|Bad ip address tries to spray connection requests on one of the popular ports (21,22,53,80,443 etc) on multiple IP addresses with an intention to find which ports are opened on what IP addresses. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle and attacker finds open port on one of ip addresses and is able to establish a connection. | |Bad ip address tries to spray connection requests on one of the popular ports (21,22,53,80,443 etc) on multiple IP addresses with an intention to find which ports are opened on what IP addresses. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle and attacker finds open port on one of ip addresses and is able to establish a connection. | ||
It is important to check the reputation of the external ip address and block the same if necessary. | It is important to check the reputation of the external ip address and block the same if necessary. | ||
| Line 298: | Line 298: | ||
|- | |- | ||
|Fortigate firewall host scan activity by malicious ip | |Fortigate firewall host scan activity by malicious ip | ||
| − | |This alert is triggered when more than 10 connections happened from same malicious IP using different destination port, within one minute | + | |This alert is triggered when more than 10 connections happened from the same malicious IP using different destination port, within one minute |
|Bad ip address tries to spray connection requests on multiple popular ports (21,22,53,80,443 etc) targetting one single IP address at a time with an intention to find the open ports on the target IP address. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle. | |Bad ip address tries to spray connection requests on multiple popular ports (21,22,53,80,443 etc) targetting one single IP address at a time with an intention to find the open ports on the target IP address. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle. | ||
It is important to check the reputation of the external ip address and block the same if necessary. | It is important to check the reputation of the external ip address and block the same if necessary. | ||
|- | |- | ||
|Fortigate firewall large data sent outside | |Fortigate firewall large data sent outside | ||
| − | | | + | |This alert is triggered when large data is sent to the external IP Address. |
|Large amount of data being sent to an external network could be an indication of data exfiltration.<br/><br/> | |Large amount of data being sent to an external network could be an indication of data exfiltration.<br/><br/> | ||
Check with the user or process which is responsible for the data being sent out and whether it was done for legitimate business reasons. This could be a false positive. | Check with the user or process which is responsible for the data being sent out and whether it was done for legitimate business reasons. This could be a false positive. | ||
|- | |- | ||
|Fortigate firewall critical message reported by firewall management software | |Fortigate firewall critical message reported by firewall management software | ||
| − | |This alert is triggered when critical level message is logged. | + | |This alert is triggered when a critical level message is logged. |
|This message is generated by the firewall itself. It may indicate some operational issue that must be addressed.<br/><br/> | |This message is generated by the firewall itself. It may indicate some operational issue that must be addressed.<br/><br/> | ||
The admin may refer to firewall manual to take required action (the issue could be related to resources, errors or equivalent). | The admin may refer to firewall manual to take required action (the issue could be related to resources, errors or equivalent). | ||
|- | |- | ||
|Fortigate firewall sweep scan attack by malicious ip | |Fortigate firewall sweep scan attack by malicious ip | ||
| − | |This alert is triggered when more than 10 connections happened from same malicious IP using different Destination IP's, within one minute | + | |This alert is triggered when more than 10 connections happened from the same malicious IP using different Destination IP's, within one minute |
|Bad ip addresses tries to spray connection requests on one of the popular ports (21,22,53,80,443 etc) on multiple IP addresses with an intention to find which ports are opened on what IP addresses. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle.<br/><br/> | |Bad ip addresses tries to spray connection requests on one of the popular ports (21,22,53,80,443 etc) on multiple IP addresses with an intention to find which ports are opened on what IP addresses. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle.<br/><br/> | ||
It is important to check the reputation of the external ip address and block the same if necessary. | It is important to check the reputation of the external ip address and block the same if necessary. | ||
|- | |- | ||
|Fortigate firewall sweep scan attack | |Fortigate firewall sweep scan attack | ||
| − | |This alert is triggered when more than 10 connections happened from same source IP to various Destination IP's,within one minute. | + | |This alert is triggered when more than 10 connections happened from the same source IP to various Destination IP's, within one minute. |
|An attacker tries to spray connection requests on one of the popular ports (21,22,53,80,443 etc) on multiple IP addresses with an intention to find which ports are opened on what IP addresses. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle.<br/><br/> | |An attacker tries to spray connection requests on one of the popular ports (21,22,53,80,443 etc) on multiple IP addresses with an intention to find which ports are opened on what IP addresses. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle.<br/><br/> | ||
Unless it is a known and legitimate IP address performing scan, it is important to block this IP. You may whitelist the known IP addresses (such as designated Vulnerability Scanner, Asset Discovery Tools etc), so as to supress the false positives. | Unless it is a known and legitimate IP address performing scan, it is important to block this IP. You may whitelist the known IP addresses (such as designated Vulnerability Scanner, Asset Discovery Tools etc), so as to supress the false positives. | ||
|- | |- | ||
|Fortigate firewall host scan attack | |Fortigate firewall host scan attack | ||
| − | |This is triggered when more than 10 connections happened from same Source and Destination IP using different destination port, within one minute | + | |This alert is triggered when more than 10 connections happened from the same Source IP and Destination IP using different destination port, within one minute |
|An attacker tries to spray connection requests on multiple popular ports (21,22,53,80,443 etc) targetting one single IP addresses at a time with an intention to find the open ports on the target IP address. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle.<br/><br/> | |An attacker tries to spray connection requests on multiple popular ports (21,22,53,80,443 etc) targetting one single IP addresses at a time with an intention to find the open ports on the target IP address. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle.<br/><br/> | ||
Unless it is a known and legitimate IP address performing the scan, it is important to block this IP. You may whitelist the known IP addresses (such as designated Vulnerability Scanner, Asset Discovery Tools etc), so as to supress the false positives. | Unless it is a known and legitimate IP address performing the scan, it is important to block this IP. You may whitelist the known IP addresses (such as designated Vulnerability Scanner, Asset Discovery Tools etc), so as to supress the false positives. | ||
|- | |- | ||
|Fortigate firewall successful host scan activity by malicious ip | |Fortigate firewall successful host scan activity by malicious ip | ||
| − | | | + | |This alert is triggered when more than 10 connections happened from the same malicious IP and status is deny followed by a successful login status using different destination port, within one minute. |
|Bad ip address tries to spray connection requests on multiple popular ports (21,22,53,80,443 etc) targetting one single IP addresses at a time with an intention to find the open ports on the target IP address. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle and attacker done successful connection on open ports.<br/><br/> | |Bad ip address tries to spray connection requests on multiple popular ports (21,22,53,80,443 etc) targetting one single IP addresses at a time with an intention to find the open ports on the target IP address. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle and attacker done successful connection on open ports.<br/><br/> | ||
It is important to check the reputation of the external ip address and block the same if necessary.<br/><br/> | It is important to check the reputation of the external ip address and block the same if necessary.<br/><br/> | ||
| Line 334: | Line 334: | ||
|- | |- | ||
|Fortigate firewall successful host scan activity | |Fortigate firewall successful host scan activity | ||
| − | |This alert is triggered when more than 10 connections happened from same Source and Destination IP and status is deny followed by successful login status using different destination port, within one minute. | + | |This alert is triggered when more than 10 connections happened from the same Source and Destination IP and status is deny followed by a successful login status using different destination port, within one minute. |
|Attacker tries to spray connection requests on multiple popular ports (21,22,53,80,443 etc) targetting one single IP addresses at a time with an intention to find the open ports on the target IP address. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle and attacker done successful connection on open ports.<br/><br/> | |Attacker tries to spray connection requests on multiple popular ports (21,22,53,80,443 etc) targetting one single IP addresses at a time with an intention to find the open ports on the target IP address. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle and attacker done successful connection on open ports.<br/><br/> | ||
It is important to check the reputation of the suspected ip address.<br/><br/> | It is important to check the reputation of the suspected ip address.<br/><br/> | ||
| Line 343: | Line 343: | ||
|- | |- | ||
|Fortigate firewall backdoor traffic detected | |Fortigate firewall backdoor traffic detected | ||
| − | |This alert is triggered when connection happened using vulnerable Destination ports like 3127,3198,6129,7080,within one minute. | + | |This alert is triggered when connection happened using vulnerable Destination ports like 3127,3198,6129,7080, within one minute. |
|This event indicates that a traffic is generated from internal machine on vulnerable ports(3127,3198,6129,7080). Typically, these ports are used by attacker to exploit vulnerable programs listening on these ports.<br/><br/> | |This event indicates that a traffic is generated from internal machine on vulnerable ports(3127,3198,6129,7080). Typically, these ports are used by attacker to exploit vulnerable programs listening on these ports.<br/><br/> | ||
Check is these ports are open and on what servers. Do you really need these ports opened?<br/><br/> | Check is these ports are open and on what servers. Do you really need these ports opened?<br/><br/> | ||
| Line 368: | Line 368: | ||
|- | |- | ||
|Fortigate firewall successful sweep scan activity | |Fortigate firewall successful sweep scan activity | ||
| − | |This alert is triggered when more than 10 connections happened from same Source IP and status is deny followed by a successful login status using different Destination IP, within one minute. | + | |This alert is triggered when more than 10 connections happened from the same Source IP and status is deny followed by a successful login status using different Destination IP, within one minute. |
|Attacker tries to spray connection requests on one of the popular ports (21,22,53,80,443 etc) on multiple IP addresses with an intention to find which ports are opened on what IP addresses. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle and attacker done successful connection on one of ip addresses.<br/><br/> | |Attacker tries to spray connection requests on one of the popular ports (21,22,53,80,443 etc) on multiple IP addresses with an intention to find which ports are opened on what IP addresses. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle and attacker done successful connection on one of ip addresses.<br/><br/> | ||
It is important to check the reputation of the suspected ip address.<br/><br/> | It is important to check the reputation of the suspected ip address.<br/><br/> | ||
Revision as of 13:05, 20 June 2019
Contents
- 1 Introduction
- 2 Enabling Syslog forwarding on the device
- 3 How to Install the KHIKA App for Fortigate Firewall?
- 4 How to get your Fortigate Firewall into KHIKA ?
- 5 Adding the device in the Adaptor
- 6 Verifying SYSLOG data collection
- 7 How to check the output of KHIKA Fortigate App ?
Introduction
Most of the network devices, such as firewalls, switches, routers, web proxies etc send the traffic and user activity related information in the form of logs over syslog protocol. Some applications such as Oracle database server, Symantec antivirus server, EMC SAN Storage etc also support syslog protocol as syslog is very efficient and simple to integrate with. KHIKA Data Aggregator is pre-configured with syslog services on port 514. The key parts to get here are :
- Enabling Syslog forwarding on the device
- Install the KHIKA App for Fortigate Firewall
- Get data from your Fortigate Firewall into KHIKA Aggregator
Enabling Syslog forwarding on the device
For help to enable the syslog forwarding go to link here
How to Install the KHIKA App for Fortigate Firewall?
It is assumed, that you have already configured KHIKA Data Aggregator in your environment. If not, please read how to configure KHIKA Data Aggregator and perform the pre-requisite steps.
This section explains how to pick and install the KHIKA application for Fortigate Firewall . Installing the application shall put together and activate the adapter (parser) that can handle Fortigate Firewall data format, the dashboards and the alert rules preconfigured.
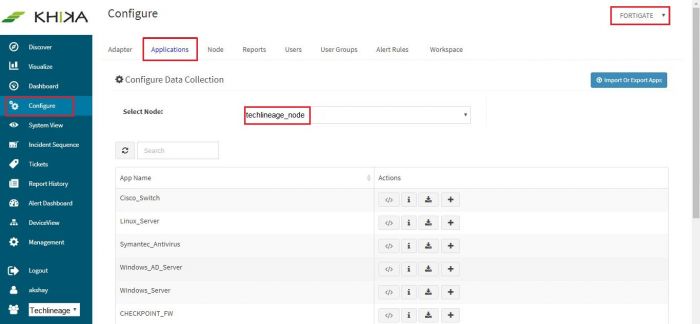
Go to “Applications” tab in the “Configure” menu.
Check whether the appropriate Workspace is selected. Note: Application is always loaded in a Workspace. Read the section on Workspaces to know more about KHIKA Workspaces. Also select your KHIKA aggregator name in the Node dropdown. This is to ensure that we are collecting data from the desired source and into the correct workspace which is ready with the configured application and components.
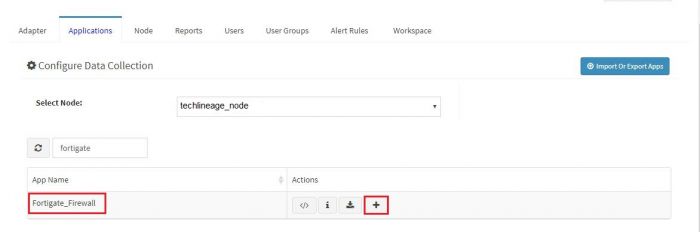
Click on the “+” button. A pop up appears.
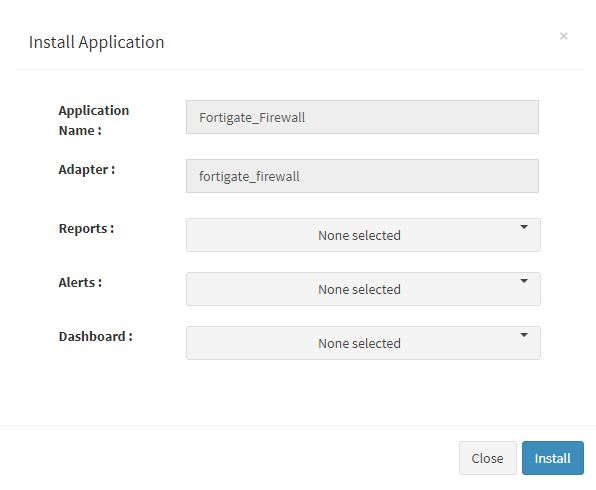
User can now select the contents of the application required. For example, on the dropdown for “Reports”, click to expand it. List of all reports can be seen. User can individually select the reports required by checking on the checkbox next to each. Alternatively, check on “Select All” option to get all of them. Similarly you can select contents from Alerts and Dashboards.
What are KHIKA Reports What are KHIKA Dashboards What are KHIKA Alerts
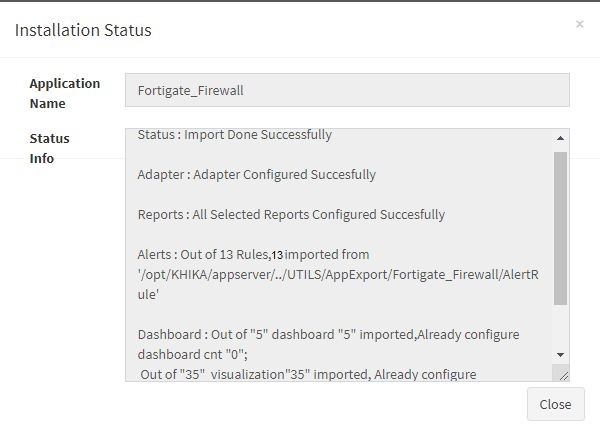
Click “OK” to proceed with the installation of the selected Application. After successful installation, following status should be displayed :
This simple procedure to install a KHIKA App, automatically configures the Adapter (required for parsing the data from raw syslogs), calculated KHIKA reports on raw data, Visualizations, Dashboards and Alerts – all in one click.
How to get your Fortigate Firewall into KHIKA ?
KHIKA recommends, popular syslog forwarding to monitor the Fortigate Firewall. You must configure the network device (or the end node) to send its logs to KHIKA Data Aggregator by providing IP address of Data Aggregator and port 514 so that the device can send its logs to KHIKA syslog service. (Please refer the documentation of individual device/vendor/OEM to understand how to configure remote syslogging for the device. Many vendors support web based configuration these days and some vendors support command based configurations)
NOTE: You will have to repeat these steps on each of the APPLICATION that you wish to monitor using KHIKA.
Adding the device in the Adaptor
For help to adding a device in the adapter click here.
Verifying SYSLOG data collection
For help to verifying syslog data collection click here.
How to check the output of KHIKA Fortigate App ?
Fortigate Firewall Attack Dashboard
Go to "Dashboards" from the left menu. From the list of in-built dashboards, select this one. It shall open the Dashboard. This dashboard focuses on the attack information like attack name and action can be taken for that attack on fortigate firewall (which are added into KHIKA). Details like action taken for that attack, attack happened while communicating with sourceIP and destinationIP etc. You can filter and search information and create new ones too. For help with Dashboards, click here
Elements in the Dashboard are explained below :
| Visualization | Description |
| Attack wise Action bar graph | X axis : Differnt types of attack on fortigate firewall Y axis : Action performed on attack and it's count. |
| Contribution of Severity and Action multi-level pie chart | Different types of Severity like critical, info, error, warning and Action(s) performed like clear_session on fortiagte firewall. |
| SourceIP wise Attack bar graph | X axis : source IP(s). Y axis : Differnt types of attack and it's count. |
| DestinationIP wise Attack bar graph | X axis : Destination IP(s). Y axis : Differnt types of attack and it's count. |
| Daily Trend | Trend of events over time. Useful to identify unusual spikes at a glance. X axis : date & time Y axis : count of events |
| Contribution of Service pie chart | Contibution of differnt types of services like https,ping on fortigate firewall. |
| Summary Table | Detailed data with timestamp and count |
Suggestion for useful interaction with this dashboard could be :
- Click on “Attack” in the "Attack wise Action" bar graph. This gets selected and shows the different types of attacks and actions taken for the selected attack. The next bar shall show sourceIP and destinationIP.The next pie shall shows different types of "severity" and "services" on the fortigate firewall. Details of the selected attack can be seen in the summary table.How to remove this filter is explained here
Fortigate Firewall MaliciousIP Dashboard
Go to "Dashboards" from the left menu. From the list of in-built dashboards, select this one. It shall open the Dashboard. This dashboard focuses on the fortigate firewall communication with suspicious IP(s). Details like KHIKA shares community based threat intelligence and detect bad IP's, Those bad Source IP/Destination IP communication with internal IP which is shown in an analytical fashion. You can filter and search information and create new ones too. For help with Dashboards, click here
Elements in the Dashboard are explained below :
| Visualization | Description |
| Contribution of Action pie chart | Contribution of the status of connection.Example allow, deny etc. |
| Malicious IP wise Action bar chart | X axis : All the MaliciousIP(s) which communicate with device Y axis : MaliciousIP wise Action and it's count. |
| SourceIP wise Hits bar graph | X axis : All the Source IP(s) which initiate the connection Y axis : SourceIP wise number of hits. |
| DestinationIP wise Hits bar graph | X axis : All the Destination IP(s) which communicate to malicious IP Y axis : DestinationIP wise number of hits. |
| Contribution of service pie chart | Contribution of different types of services like snmp of fortigate firewall. |
| Contribution of level pie chart | Contribution of different types of levels like notice of fortigate firewall. |
| Daily Trend | Trend of events over time. Useful to identify unusual spikes at a glance. X axis : date & time Y axis : count of events |
| Summary Table | Detailed data with timestamp and count |
A suggestion for useful interaction with this dashboard could be :
- Click on “MaliciousIP” in the "Malicious IP wise Action" bar graph. This gets selected and shows the actions for selected Malicious IP.The next bar shall show Source IP and Destination IP for selected malicious communication.The next pie shall show different types of "action", "services" and "levels" for selected Malicious IP. Details about selected Malicious IP can be seen in the summary table.How to remove this filter is explained here
Fortigate Firewall System Activities Dashboard
Go to "Dashboards" from the left menu. From the list of in-built dashboards, select this one. It shall open the Dashboard. This dashboard summarizes self monitoring system event and also command,action executed by user etc.
You can filter and search information and create new ones too. For help with Dashboards, click here
Elements in the Dashboard are explained below :
| Visualization | Description |
| Contribution of Action pie chart | Contribution of action performed by a particular user on the fortigate firewall. |
| User wise Action bar graph | X axis : user(s) Y Axis : Action performed by a particular user and it's count. |
| Contribution of Status pie chart | Contribution of different types of status. |
| Contribution of level pie chart | Contribution of different types of levels like notice, warning, etc. for event |
| LogDesc wise Message bar graph | X axis : Logdesc Y axis : Logdesc wise message and it's count. |
| Daily Trend | Trend of events over time. Useful to identify unusual spikes at a glance. X axis : date & time Y axis : count of events |
| Summary Table | Detailed data with timestamp and count |
Some suggestions for useful interaction with this dashboard could be :
- Click on “User” in the "User wise Action" bar graph. This gets selected and shows the action performed by selected User on fortigate firewall.The next bar shall show messages for selected User on fortigate firewall. The next pie shall shows differnt types of "status","action" and "levels".Details of all activities performed by selected user can be seen in the summary table.How to remove this filter is explained here
Fortigate Firewall VPN Dashboard
Go to "Dashboards" from the left menu. From the list of in-built dashboards, select this one. It shall open the Dashboard.This dashboard focuses on the VPN login activities on fortigate firewall. Details like type of VPN, Source IP,Destination IP etc.
You can filter and search information and create new ones too. For help with Dashboards, click here
Elements in the Dashboard are explained below :
| Visualization | Description |
| Contribution of VPN pie chart | Contribution of different types of VPN on fortigate firewall. |
| Contribution of VPN Type pie chart | Contribution of different types VPN type on fortigate firewall. |
| SourceIP wise Hits | X axis : SourceIP(s) Y axis : SourceIP wise number of hits. |
| DestinationIP wise Hits | X axis : DestinationIP(s) Y axis : DestinationIP wise number of hits. |
| Contribution of Service pie chart | Contribution of different types of services like snmp,syslog of fortigate firewall. |
| Daily Trend | Trend of events over time. Useful to identify unusual spikes at a glance. X axis : date & time Y axis : count of events |
| Summary Table | Detailed data with timestamp and count |
Some suggestions for useful interaction with this dashboard could be :
- Click on particular VPN tunnel in the "Contribution of VPN" pie chart. This gets selected and shows the VPN name.The next bar shall show sourceIP which intiate VPN connection and destinationIP(server IP) which is accessed by Source IP. The next pie shall shows differnt types of "VPN types" and "services" of fortigate firewall.Details of selected VPN information can be seen in the summary table.How to remove this filter is explained here
Fortigate Firewall VPNTunnel Dashboard
Go to "Dashboards" from the left menu. From the list of in-built dashboards, select this one. It shall open the Dashboard. This dashboard focuses on the VPN Tunnel information like VPN Tunnel , Status etc.You can filter and search information and create new ones too. For help with Dashboards, click here
Elements in the Dashboard are explained below :
| Visualization | Description |
| Contribution of VPN Tunnel pie chart | Contribution of differnt VPN Tunnel on fortigate firewall. |
| Contribution of Status pie chart | Contribution of status like sucess/failure. |
| Remote IP wise Hits bar graph | X axis : Remote IP(s) Y axis : Remote IP wise number of hits. |
| Local IP wise Hits bar graph | X axis : Local IP(s) Y axis : Local IP wise number of hits. |
| Daily Trend | Trend of events over time. Useful to identify unusual spikes at a glance. X axis : date & time Y axis : count of events |
| Summary Table | Detailed data with timestamp and count |
Some suggestions for useful interaction with this dashboard could be :
- Click on “VPN Type” in the "Contribution of VPN Tunnel" bar graph. This gets selected and shows the VPN Tunnel information . The next bar shall show RemoteIP which is a Source IP and LocalIP which is accessed by remotely. The next pie shall shows different types of status like sucess/failue on fortigate firewall.Details about selected VPN Traffric can be seen in the summary table. How to remove this filter is explained here
Fortigate Firewall Alerts
Alerts are generated when certain ciritical behaviour is observed in the system – real time and notified on the Alerts Dashboard in KHIKA as well as can be received in email to relevant stakeholders. The details of KHIKA Alerts are mentioned here Click on “Alert Dashboard” on left menu.
Certain alerts for fortigate firewall are pre-canned and shipped with KHIKA, keeping in mind the requirements of the users. They are mentioned in the table below :
Alerts Description
| Alert Name | Description | Suggested Resolution |
| Fortigate firewall successful sweep scan activity by malicious ip | This alert is triggered when more than 10 connections happened from same malicious IP and status is deny followed by a successful login status using different Destination IP, within one minute | Bad ip address tries to spray connection requests on one of the popular ports (21,22,53,80,443 etc) on multiple IP addresses with an intention to find which ports are opened on what IP addresses. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle and attacker finds open port on one of ip addresses and is able to establish a connection.
It is important to check the reputation of the external ip address and block the same if necessary. It is also important to verify the sanity of affected internal nodes by checking if any unwarranted system policy change or software configuration/updates have occured during the affected time period. If required, quarantine the affected servers till the time the issues are resolved. |
| Fortigate firewall host scan activity by malicious ip | This alert is triggered when more than 10 connections happened from the same malicious IP using different destination port, within one minute | Bad ip address tries to spray connection requests on multiple popular ports (21,22,53,80,443 etc) targetting one single IP address at a time with an intention to find the open ports on the target IP address. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle.
It is important to check the reputation of the external ip address and block the same if necessary. |
| Fortigate firewall large data sent outside | This alert is triggered when large data is sent to the external IP Address. | Large amount of data being sent to an external network could be an indication of data exfiltration. Check with the user or process which is responsible for the data being sent out and whether it was done for legitimate business reasons. This could be a false positive. |
| Fortigate firewall critical message reported by firewall management software | This alert is triggered when a critical level message is logged. | This message is generated by the firewall itself. It may indicate some operational issue that must be addressed. The admin may refer to firewall manual to take required action (the issue could be related to resources, errors or equivalent). |
| Fortigate firewall sweep scan attack by malicious ip | This alert is triggered when more than 10 connections happened from the same malicious IP using different Destination IP's, within one minute | Bad ip addresses tries to spray connection requests on one of the popular ports (21,22,53,80,443 etc) on multiple IP addresses with an intention to find which ports are opened on what IP addresses. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle. It is important to check the reputation of the external ip address and block the same if necessary. |
| Fortigate firewall sweep scan attack | This alert is triggered when more than 10 connections happened from the same source IP to various Destination IP's, within one minute. | An attacker tries to spray connection requests on one of the popular ports (21,22,53,80,443 etc) on multiple IP addresses with an intention to find which ports are opened on what IP addresses. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle. Unless it is a known and legitimate IP address performing scan, it is important to block this IP. You may whitelist the known IP addresses (such as designated Vulnerability Scanner, Asset Discovery Tools etc), so as to supress the false positives. |
| Fortigate firewall host scan attack | This alert is triggered when more than 10 connections happened from the same Source IP and Destination IP using different destination port, within one minute | An attacker tries to spray connection requests on multiple popular ports (21,22,53,80,443 etc) targetting one single IP addresses at a time with an intention to find the open ports on the target IP address. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle. Unless it is a known and legitimate IP address performing the scan, it is important to block this IP. You may whitelist the known IP addresses (such as designated Vulnerability Scanner, Asset Discovery Tools etc), so as to supress the false positives. |
| Fortigate firewall successful host scan activity by malicious ip | This alert is triggered when more than 10 connections happened from the same malicious IP and status is deny followed by a successful login status using different destination port, within one minute. | Bad ip address tries to spray connection requests on multiple popular ports (21,22,53,80,443 etc) targetting one single IP addresses at a time with an intention to find the open ports on the target IP address. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle and attacker done successful connection on open ports. It is important to check the reputation of the external ip address and block the same if necessary. |
| Fortigate firewall successful host scan activity | This alert is triggered when more than 10 connections happened from the same Source and Destination IP and status is deny followed by a successful login status using different destination port, within one minute. | Attacker tries to spray connection requests on multiple popular ports (21,22,53,80,443 etc) targetting one single IP addresses at a time with an intention to find the open ports on the target IP address. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle and attacker done successful connection on open ports. It is important to check the reputation of the suspected ip address. |
| Fortigate firewall backdoor traffic detected | This alert is triggered when connection happened using vulnerable Destination ports like 3127,3198,6129,7080, within one minute. | This event indicates that a traffic is generated from internal machine on vulnerable ports(3127,3198,6129,7080). Typically, these ports are used by attacker to exploit vulnerable programs listening on these ports. Check is these ports are open and on what servers. Do you really need these ports opened? |
| Fortigate firewall communication with possible IOC or bad IP | This alert is triggered when suspicious IP is communication with internal IP | KHIKA shares community based threat intelligence (TI) every 24 hours. TI has list of IP addresses with bad reputation. Every bad IP is marked with number of communities reporting it, name of each community and confidence indicating how confident are we about the reputation. This alert is generated when communication with a bad IP is let through. If communication with a bad IP is happening, it must be blocked immediately as it could be a possible attack or data exfiltration. |
| Fortigate firewall communication with suspicious IP | This alert is triggered when bytes are send and receive during communication with maliacious IP. | Communication with a bad IP is happening, it must be blocked immediately as it could be a possible attack or data exfiltration.
You can check the log for this communication by simply searching the malicious IP in the logs. You can also check which internal IP addresses are communicating with this IP address and track the real users behind those internal IP addresses. |
| Fortigate firewall successful sweep scan activity | This alert is triggered when more than 10 connections happened from the same Source IP and status is deny followed by a successful login status using different Destination IP, within one minute. | Attacker tries to spray connection requests on one of the popular ports (21,22,53,80,443 etc) on multiple IP addresses with an intention to find which ports are opened on what IP addresses. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle and attacker done successful connection on one of ip addresses. It is important to check the reputation of the suspected ip address. |