Difference between revisions of "KHIKA App for Checkpoint Firewall"
Onkar pawar (talk | contribs) (→How to Install the KHIKA App for Checkpoint Firewall ?) |
(→Alerts Description) |
||
| (103 intermediate revisions by 3 users not shown) | |||
| Line 1: | Line 1: | ||
== Introduction == | == Introduction == | ||
| − | + | ||
| − | Checkpoint Firewall | + | Firewalls are used to control the peripheral traffic and communication in organisations and hence its essential and critical to monitor them. |
| + | Checkpoint Firewall sends the traffic and user activity related information in the form of logs over syslog protocol. KHIKA Data Aggregator is pre-configured with syslog services on port 514. | ||
| + | |||
The key parts to get here are : | The key parts to get here are : | ||
| − | #Enabling Syslog forwarding on the device | + | #Enabling Syslog forwarding on the firewall device |
#Install the KHIKA App for Checkpoint Firewall | #Install the KHIKA App for Checkpoint Firewall | ||
| − | #Get data from your Checkpoint Firewall into KHIKA Aggregator | + | #Get data from your Checkpoint Firewall into the KHIKA Aggregator |
== Enabling Syslog forwarding on the device == | == Enabling Syslog forwarding on the device == | ||
| − | [[Getting Data into KHIKA# | + | Please refer [https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk122323 here] for enabling syslogs on your Checkpoint firewall device. |
| + | |||
| + | Example of a command to be fired on Firewall Device to enable syslogs: | ||
| + | cp_log_export add name <name> [domain-server <domain-server>] target-server <target-server IP address> target-port <target-port> protocol <(udp|tcp)> format <(syslog)|(cef)|(splunk)(generic)> | ||
| + | |||
| + | name :Unique name of the exporter configuration. | ||
| + | domain-server :The relevant domain-server name or IP | ||
| + | target-server :Exporting the logs to this ip address | ||
| + | target-port :The port on which the target is listening to.Here use port 514 | ||
| + | protocol :Transport protocol to use.Here use protocol udp | ||
| + | format :The format in which the logs will be exported .Here use format cef | ||
| + | |||
| + | == Verifying SYSLOG data collection == | ||
| + | |||
| + | After you enable the syslog forwarding on the end device, you must verify if the logs are being really received by KHIKA Data Aggregator. Please refer [[Getting Data into KHIKA#Verifying syslog data collection|here]] to understand how to verify syslogs on KHIKA Data Aggregator. | ||
== How to Install the KHIKA App for Checkpoint Firewall ? == | == How to Install the KHIKA App for Checkpoint Firewall ? == | ||
| Line 14: | Line 30: | ||
It is assumed, that you have already configured KHIKA Data Aggregator in your environment. If not, please read [[Getting Started with KHIKA SaaS#Installing and configuring KHIKA Data Aggregator|how to configure KHIKA Data Aggregator]] and perform the pre-requisite steps. | It is assumed, that you have already configured KHIKA Data Aggregator in your environment. If not, please read [[Getting Started with KHIKA SaaS#Installing and configuring KHIKA Data Aggregator|how to configure KHIKA Data Aggregator]] and perform the pre-requisite steps. | ||
| − | This section explains how to pick and install the KHIKA application for Checkpoint Firewall . Installing the application shall put together and activate the adapter (parser) that can handle Checkpoint Firewall data format, the dashboards and the alert rules preconfigured. | + | This section explains how to pick and install the KHIKA application for Checkpoint Firewall. Installing the application shall put together and activate the adapter (parser) that can handle Checkpoint Firewall data format, the dashboards and the alert rules preconfigured. |
| + | |||
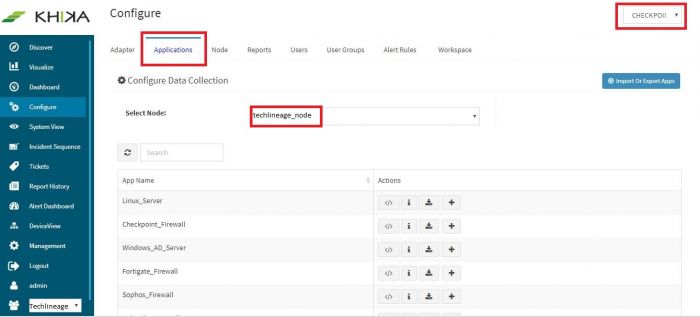
| + | Go to “Applications” tab in the “Configure” menu. | ||
| − | [[ | + | [[File:checkpoint_applicationtab.JPG|700px]] |
| − | + | Check whether the appropriate Workspace is selected. | |
| + | Note: Application is always loaded in a Workspace. Read the section on [[Accessing the KHIKA Gui#Creating a Workspace|Workspaces]] to know more about KHIKA Workspaces. | ||
| + | Also select your KHIKA aggregator name in the Node dropdown. | ||
| + | This is to ensure that we are collecting data from the desired source and into the correct workspace which is ready with the configured application and components. | ||
| − | + | [[File:checkpoint_fwapp_name.jpg|700px]] | |
| − | |||
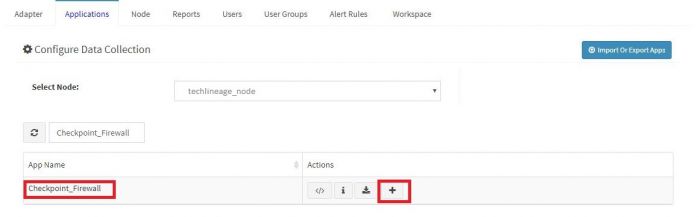
| − | + | Click on the “+” button next to the Checkpoint Firewall App. A pop up appears. | |
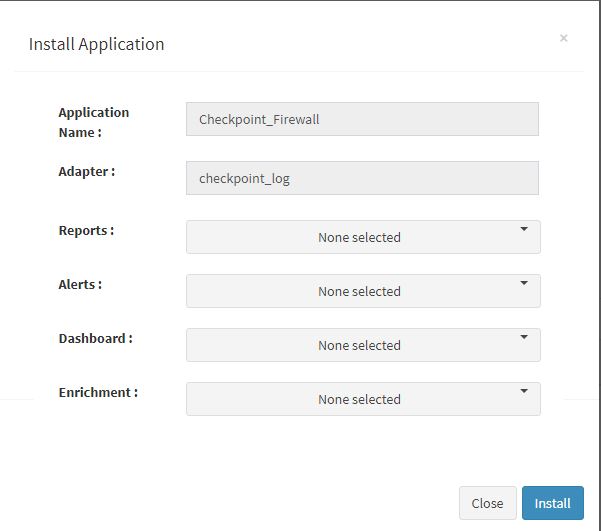
| + | |||
| + | [[File:checkpoint_app_install.JPG|700px]] | ||
| + | |||
| + | User can now select the contents of the application required. For example, on the dropdown for “Reports”, click to expand it. List of all reports can be seen. User can individually select the reports required by checking on the checkbox next to each. Alternatively, check on “Select All” option to get all of them. | ||
| + | Similarly you can select contents from Alerts and Dashboards. | ||
| + | |||
| + | Visit the sections on [[KHIKA Reports| KHIKA Reports]], [[KHIKA Dashboards| KHIKA Dashboards]], [[KHIKA Alerts & Correlations| KHIKA Alerts & Correlations]] to know more about these topics. | ||
| + | |||
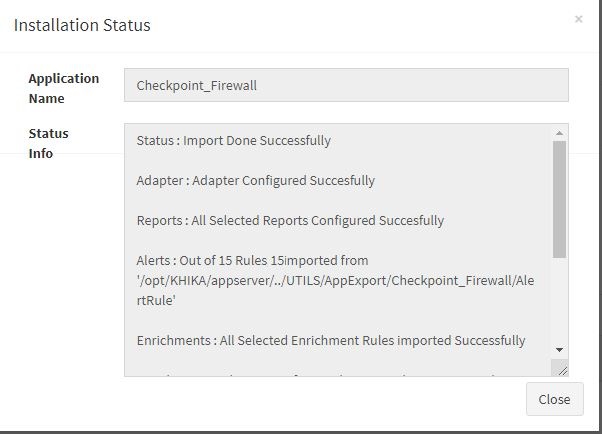
| + | Click “OK” to proceed with the installation of the selected Application. | ||
| + | After successful installation, following status should be displayed : | ||
| + | |||
| + | [[File:checkpoint_app_installation_status.JPG|700px]] | ||
| + | |||
| + | This simple procedure to install a KHIKA App, automatically configures the Adapter (required for parsing the data from raw syslogs), calculated KHIKA reports on raw data, Visualizations, Dashboards and Alerts – all in one click. | ||
== Adding the device in the Adaptor == | == Adding the device in the Adaptor == | ||
| + | After syslogs are enabled on the device and the App is installed into KHIKA, it is the time to add the device to the this App (in Adapter section of KHIKA Web GUI). Please refer [[Getting Data into KHIKA#Adding device details in the Adaptor|here]] to know [[Getting Data into KHIKA#Adding device details in the Adaptor|how to add the device to an App]]. | ||
| + | |||
| + | After making these configuration in KHIKA, you must apply these changes to the Workspace. Go to Configure, select the Workspace and in Workspace tab of configure menu press the Apply button as shown in the screenshot below. | ||
| + | |||
| + | [[File:checkpoint_apply_configuration.JPG|800px]] | ||
| − | |||
| − | + | Wait for a few minutes for changes to apply and data to arrive in kHIKA. With all these steps, we should now expect the data to arrive in KHIKA. Lets discover some live data in KHIKA. | |
| − | |||
== How to check the output of KHIKA Checkpoint Firewall App ? == | == How to check the output of KHIKA Checkpoint Firewall App ? == | ||
| − | === | + | ===Discovering the logs of Checkpoint Firewall=== |
| + | After doing all the steps given above, we should start receiving live data into KHIKA. Go to "Discover" section in KHIKA GUI and select the index with name "*raw-checkpoint_firewall*". Note that the index has a prefix of the customer name and workspace name. After selecting this index, you should see the live data coming in. Spend some time understanding this data and the fields of the data. | ||
| + | |||
| + | === Checkpoint Firewall Malicious Communication Dashboard=== | ||
| − | Go to "Dashboards" from the left menu. From the list of in-built dashboards, select this one. It shall open the Dashboard. This dashboard focuses on the Checkpoint Firewall communication with suspicious | + | Go to "Dashboards" from the left menu. From the list of in-built dashboards, select this one. It shall open the Dashboard. |
| − | You can filter and search information and create new ones too. For help with Dashboards, click [[KHIKA Dashboards|here]] | + | |
| + | This dashboard focuses on the Checkpoint Firewall communication with suspicious IP addresses and it's traffic status(which is added into KHIKA).Details like the malicious IP address,the source IP and destination IP at that time, actions, service, traffic direction etc. is shown in an analytical fashion. | ||
| + | You can filter and search information and create new visualizations ones too. | ||
| + | |||
| + | For help with Dashboards, click [[KHIKA Dashboards|here]] | ||
==== Elements in the Dashboard are explained below : ==== | ==== Elements in the Dashboard are explained below : ==== | ||
{| class="wikitable" | {| class="wikitable" | ||
| − | |+ style="caption-side:bottom; color:#e76700;"|''Elements in " | + | |+ style="caption-side:bottom; color:#e76700;"|''Elements in "Checkpoint Firewall Malicious Communication" Dashboard'' |
|- | |- | ||
|'''Visualization''' | |'''Visualization''' | ||
|'''Description''' | |'''Description''' | ||
|- | |- | ||
| − | |Contribution of Action | + | |Contribution of Action |
| − | |Contribution of actions during communication with malicious | + | |Contribution of actions during communication with malicious IPs |
|- | |- | ||
|Contribution of Malicious IP | |Contribution of Malicious IP | ||
| − | |Contribution of Malicious IP | + | |Contribution of Malicious IP addresses, according to no. of events occured in logs. |
|- | |- | ||
|Malicious IP wise Action | |Malicious IP wise Action | ||
| − | |X axis : All Malicious | + | |X axis : All Malicious IPs communicated through the firewall<br/> |
| − | Y axis : Actions stacked in one bar(Malicious IP) and | + | Y axis : Actions stacked in one bar(Malicious IP) and their count |
|- | |- | ||
|Source IP wise Hits | |Source IP wise Hits | ||
| − | |X axis : | + | |X axis : Source IPs found in Malicious Communication<br/> |
| − | Y axis : The count of Source | + | Y axis : The count of Source IPs during Malicious Communication |
|- | |- | ||
|Destination IP wise Hits | |Destination IP wise Hits | ||
| − | |X axis : | + | |X axis : Destination IPs found in Malicious Communication<br/> |
Y axis : The count of Destination IP during Malicious Communication | Y axis : The count of Destination IP during Malicious Communication | ||
|- | |- | ||
| Line 73: | Line 117: | ||
|} | |} | ||
| − | ==== | + | ==== Suggestions for useful interaction with this dashboard could be : ==== |
| + | |||
| + | #Select a particular malicious IP from the Contribution of Malicious IP pie. Rest of the visualizations reflect all source IP, destination IP and actions with respect to this malicious IP. | ||
| + | #Select an action from Contribution of Action pie. You can check what traffic gets accepted and wether it is from any particular source or unusually high at any time of the day and so on. | ||
| + | |||
| + | === Checkpoint Firewall Triggered Signature Dashboard=== | ||
| − | + | Go to "Dashboards" from the left menu. From the list of in-built dashboards, select this one. It shall open the Dashboard. | |
| − | |||
| − | + | This dashboard gives attack information against predefined signatures of attacks. It includes information about source and destination IPs and also possible malicious IPs among them. What action has been taken by firewall on each is also present. | |
| + | You can filter and search information and create new visualizations too. | ||
| − | + | For help with Dashboards, click [[KHIKA Dashboards|here]] | |
| − | |||
==== Elements in the Dashboard are explained below : ==== | ==== Elements in the Dashboard are explained below : ==== | ||
{| class="wikitable" | {| class="wikitable" | ||
| − | |+ style="caption-side:bottom; color:#e76700;"|''Elements in " | + | |+ style="caption-side:bottom; color:#e76700;"|''Elements in "Checkpoint Firewall Triggered Signature" Dashboard'' |
|- | |- | ||
|'''Visualization''' | |'''Visualization''' | ||
|'''Description''' | |'''Description''' | ||
|- | |- | ||
| − | |Contribution of Action | + | |Contribution of Action |
| − | |Contribution of Actions | + | |Contribution of Actions in signatures of attacks |
|- | |- | ||
| − | |Contribution of Attack | + | |Contribution of Attack |
| − | |Contribution of | + | |Contribution of Attacks according to no. of events occured |
|- | |- | ||
|Source IP wise Attack Hits | |Source IP wise Attack Hits | ||
| − | |X axis : | + | |X axis : Source IPs found during Attack<br/> |
| − | Y axis : Stacked within each bar (ie. for each | + | Y axis : Stacked within each bar (ie. for each Attack) the Source IP and count of events |
|- | |- | ||
|Destination IP wise Attack Hits | |Destination IP wise Attack Hits | ||
| − | |X axis : All the Source | + | |X axis : All the Source IPs during Signature Attack<br/> |
| − | Y axis : Stacked within each bar (ie. for each | + | Y axis : Stacked within each bar (ie. for each Attack) the Destination IP and count of events |
|- | |- | ||
|Daily trend | |Daily trend | ||
| − | |Trend of | + | |Trend of attack events over time. Useful to identify unusual spikes at a glance. <br/><br/>X axis : date & time <br/>Y axis : count of events |
|- | |- | ||
|Summary Table | |Summary Table | ||
| Line 113: | Line 161: | ||
|} | |} | ||
| − | ==== | + | ==== Suggestions for useful interaction with this dashboard could be : ==== |
| − | #Click on | + | #Click on or select a particular attack in the Contribution of Attack pie. The rest of the dashboard reflects all source IPs,destination IPs and actions with respect to selected attack. |
| − | #For | + | #For more granular detection select particular action from Contribution of Action pie chart, now rest of the dashboard will reflect accordingly. |
=== Chekpoint Firewall VPN Activity Dashboard=== | === Chekpoint Firewall VPN Activity Dashboard=== | ||
| − | Go to "Dashboards" from the left menu. From the list of in-built dashboards, select this one. It shall open the Dashboard. This dashboard gives Checkpoint Firewall VPN activity details | + | Go to "Dashboards" from the left menu. From the list of in-built dashboards, select this one. It shall open the Dashboard. |
| + | |||
| + | This dashboard gives Checkpoint Firewall VPN activity details like Source IP, Destination IP, VPN user, Interface Name, Policy Name, Interface Direction etc. in analytical fashion. | ||
You can filter and search information and create new ones too. For help with Dashboards, click [[KHIKA Dashboards|here]] | You can filter and search information and create new ones too. For help with Dashboards, click [[KHIKA Dashboards|here]] | ||
| Line 126: | Line 176: | ||
{| class="wikitable" | {| class="wikitable" | ||
| − | |+ style="caption-side:bottom; color:#e76700;"|''Elements in " | + | |+ style="caption-side:bottom; color:#e76700;"|''Elements in "Checkpoint Firewall VPN Activity" Dashboard'' |
|- | |- | ||
|'''Visualization''' | |'''Visualization''' | ||
| Line 132: | Line 182: | ||
|- | |- | ||
|Contribution of VPN User pie chart | |Contribution of VPN User pie chart | ||
| − | |Contribution of VPN User | + | |Contribution of VPN User according to no. of events occured |
|- | |- | ||
|Contribution of Action pie chart | |Contribution of Action pie chart | ||
| − | |Contribution of Actions | + | |Contribution of Actions taken on VPN traffic |
|- | |- | ||
|Source IP wise Hits | |Source IP wise Hits | ||
| − | |X axis : | + | |X axis : Source IPs found during VPN Activity<br/> |
| − | Y axis : The count of Source | + | Y axis : The count of Source IPs during VPN |
|- | |- | ||
|Destination IP wise Hits | |Destination IP wise Hits | ||
| − | |X axis : All the Source | + | |X axis : All the Source IPs during VPN Activityk<br/> |
Y axis : The count of Destination IP during VPN | Y axis : The count of Destination IP during VPN | ||
|- | |- | ||
| Line 161: | Line 211: | ||
==== A suggestion for useful interaction with this dashboard could be : ==== | ==== A suggestion for useful interaction with this dashboard could be : ==== | ||
| − | #Click on and select a particular user in the | + | #Click on and select a particular user in the Contribution of User pie. The rest of the visualization reflects all source IPs,destination IPs,policies,actions etc. with respect to selected VPN user. |
| − | # | + | #Click on and select particular action in the Contribution of Action pie. Now rest of the visualizations will reflect accordingly. |
| − | === | + | === Checkpoint Firewall Attack Dashboard=== |
| − | Go to "Dashboards" from the left menu. From the list of in-built dashboards, select this one. It shall open the Dashboard. This dashboard gives Checkpoint Firewall attack information | + | Go to "Dashboards" from the left menu. From the list of in-built dashboards, select this one. It shall open the Dashboard. |
| − | You can filter and search information and create new | + | |
| + | This dashboard gives Checkpoint Firewall attack information. You can filter and search information and create new visualizations too. | ||
| + | |||
| + | For help with Dashboards, click [[KHIKA Dashboards|here]] | ||
==== Elements in the Dashboard are explained below : ==== | ==== Elements in the Dashboard are explained below : ==== | ||
{| class="wikitable" | {| class="wikitable" | ||
| − | |+ style="caption-side:bottom; color:#e76700;"|''Elements in " | + | |+ style="caption-side:bottom; color:#e76700;"|''Elements in "Checkpoint Firewall Attack" Dashboard'' |
|- | |- | ||
|'''Visualization''' | |'''Visualization''' | ||
|'''Description''' | |'''Description''' | ||
|- | |- | ||
| − | |||
|Contribution of Attack | |Contribution of Attack | ||
| + | |Contribution of Attacks according to the occurence | ||
|- | |- | ||
| − | |Contribution of Malicious IP | + | |Contribution of Malicious IP |
| − | |Contribution of Malicious | + | |Contribution of Malicious IPs in Attack events |
|- | |- | ||
|Attack wise Attack Info | |Attack wise Attack Info | ||
| − | |X axis : | + | |X axis : Attacks accross Firewall <br/> |
Y axis : Stacked within each bar (ie. for each Attack info) the Attack Name and count of events | Y axis : Stacked within each bar (ie. for each Attack info) the Attack Name and count of events | ||
|- | |- | ||
| − | |Source IP wise | + | |Source IP wise Attack |
| − | |X axis : | + | |X axis : Source IPs found during Signature Attack<br/> |
Y axis : Stacked within each bar (ie. for each Attack) the Source IP and count of events | Y axis : Stacked within each bar (ie. for each Attack) the Source IP and count of events | ||
|- | |- | ||
| − | |Destination IP wise | + | |Destination IP wise Attack |
|X axis : All the Source IP during Signature Attack<br/> | |X axis : All the Source IP during Signature Attack<br/> | ||
Y axis : Stacked within each bar (ie. for each Attack) the Destination IP and count of events | Y axis : Stacked within each bar (ie. for each Attack) the Destination IP and count of events | ||
| Line 203: | Line 256: | ||
|} | |} | ||
| − | ==== | + | ==== Suggestions for useful interaction with this dashboard could be : ==== |
| + | |||
| + | #Click on and select a particular attack from contribution of attack pie chart. The rest of the visualization reflects information like source IP,destination IP and attack info with respect to selected Attack. | ||
| + | #Select particular source IP in the Source wise attack bar chart. Now rest of the visualizations will reflect accordingly. | ||
| − | + | === Checkpoint Firewall Audit Admin login Dashboard=== | |
| − | |||
| − | + | Go to "Dashboards" from the left menu. From the list of dashboards, select this one. It shall open the Dashboard. This shows Checkpoint Firewall login information. It shows status of logins, from where user has logged in, which product is used for login (product like smart dashboard,smart view tracker, smart view monitor etc). You can filter and search information and create new visualizations too. | |
| − | + | For help with Dashboards, click [[KHIKA Dashboards|here]] | |
| − | |||
==== Elements in the Dashboard are explained below : ==== | ==== Elements in the Dashboard are explained below : ==== | ||
{| class="wikitable" | {| class="wikitable" | ||
| − | |+ style="caption-side:bottom; color:#e76700;"|''Elements in " | + | |+ style="caption-side:bottom; color:#e76700;"|''Elements in "Checkpoint Firewall Audit Admin login" Dashboard'' |
|- | |- | ||
|'''Visualization''' | |'''Visualization''' | ||
|'''Description''' | |'''Description''' | ||
|- | |- | ||
| − | |Contribution of Status | + | |Contribution of Status |
| − | |Contribution of status like success, | + | |Contribution of status like success,failure etc in admin user login events |
|- | |- | ||
| − | |Contribution of Machine | + | |Contribution of Machine |
|Machine Name from where admin user was trying to login | |Machine Name from where admin user was trying to login | ||
|- | |- | ||
|Admin user wise Status: | |Admin user wise Status: | ||
| − | |X axis : Admin users who | + | |X axis : Admin users who have login into Firewall<br/> |
Y axis : Admin users wise login failed and success status and its count | Y axis : Admin users wise login failed and success status and its count | ||
|- | |- | ||
| Line 243: | Line 297: | ||
|} | |} | ||
| − | ==== | + | ==== Suggestions for useful interaction with this dashboard could be : ==== |
| + | |||
| + | #Click on and select a particular status from contribution of Status pie. The rest of the visualization reflects for all Admin users the Machine Names and Client Names for selected status | ||
| + | #Select particular Admin user in Admin wise status bar. Now rest of the visualizations will reflect accordingly. | ||
| + | |||
| + | === Checkpoint Firewall Allowed External Source Dashboard=== | ||
| − | + | Go to "Dashboards" from the left menu. From the list of in-built dashboards, select this one. It shall open the Dashboard. This dashboard shows traffic which the Checkpoint Firewall allowed from external sources. Here traffic origin is external and is accepted by firewall. This dashboard gives you a control over all the external incoming traffic through your peripheral firewall. | |
| − | |||
| − | + | You can filter and search information and create new visualizations too. | |
| − | + | For help with Dashboards, click [[KHIKA Dashboards|here]] | |
| − | |||
==== Elements in the Dashboard are explained below : ==== | ==== Elements in the Dashboard are explained below : ==== | ||
{| class="wikitable" | {| class="wikitable" | ||
| − | |+ style="caption-side:bottom; color:#e76700;"|''Elements in " | + | |+ style="caption-side:bottom; color:#e76700;"|''Elements in "Checkpoint Firewall Allowed External Source Dashboard" Dashboard'' |
|- | |- | ||
|'''Visualization''' | |'''Visualization''' | ||
|'''Description''' | |'''Description''' | ||
|- | |- | ||
| − | |Contribution of Protocol | + | |Contribution of Protocol |
| − | |Contribution Protocol in allowed external | + | |Contribution Protocol in allowed traffic from external sources |
|- | |- | ||
| − | |Contribution of Services | + | |Contribution of Services |
| − | | | + | |Contribution of Services in allowed traffic from external sources |
|- | |- | ||
| − | |Source IP wise Hits | + | |Source IP wise Hits |
| − | |X axis : All Source IP in allowed external | + | |X axis : All Source IP found in allowed traffic from external sources <br/> |
| − | Y axis : Source IP wise | + | Y axis : Source IP wise events count |
|- | |- | ||
| − | |Destination IP wise Hits | + | |Destination IP wise Hits |
| − | |X axis : All Source IP in allowed external | + | |X axis : All Source IP in allowed traffic from external sources <br/> |
| − | Y axis : Destination IP wise | + | Y axis : Destination IP wise events count |
|- | |- | ||
|Daily trend | |Daily trend | ||
| Line 283: | Line 340: | ||
|} | |} | ||
| − | ==== | + | ==== Suggestions for useful interaction with this dashboard could be : ==== |
| − | #Click on and select a particular service from Contribution of Services pie. The rest of the visualization reflects all Source IP,Destination IP,Protocol etc info with | + | #Click on and select a particular service from Contribution of Services pie chart. The rest of the visualization reflects all Source IP,Destination IP,Protocol etc info with respect to selected service. |
| − | #For further | + | #For further granular detection click on and select particular Source IP or Destination IP from Source IP wise Hits and Destination IP wise Hits bar chart res.Now rest of the visualization will reflect accordingly. |
| − | === | + | === Checkpoint Firewall Blocked External Source Dashboard=== |
| − | Go to "Dashboards" from the left menu. From the list of | + | Go to "Dashboards" from the left menu. From the list of dashboards, select this one. It shall open the Dashboard. This dashboard shows traffic blocked by the Checkpoint Firewall from external sources. Here traffic origin is external and this traffic is blocked by the firewall. |
You can filter and search information and create new ones too. For help with Dashboards, click [[KHIKA Dashboards|here]] | You can filter and search information and create new ones too. For help with Dashboards, click [[KHIKA Dashboards|here]] | ||
| Line 296: | Line 353: | ||
{| class="wikitable" | {| class="wikitable" | ||
| − | |+ style="caption-side:bottom; color:#e76700;"|''Elements in " | + | |+ style="caption-side:bottom; color:#e76700;"|''Elements in "Checkpoint Firewall Blocked External Source" Dashboard'' |
|- | |- | ||
|'''Visualization''' | |'''Visualization''' | ||
|'''Description''' | |'''Description''' | ||
|- | |- | ||
| − | |Contribution of Protocol | + | |Contribution of Protocol |
| − | |Contribution Protocol in blocked external | + | |Contribution Protocol in blocked traffic from external sources |
|- | |- | ||
| − | |Contribution of Services | + | |Contribution of Services |
| − | |Contribution of Services in blocked external | + | |Contribution of Services in blocked traffic from external sources |
|- | |- | ||
| − | |Source IP wise Hits | + | |Source IP wise Hits |
|X axis : All Source IP in blocked external source traffic <br/> | |X axis : All Source IP in blocked external source traffic <br/> | ||
| − | Y axis : Source IP wise | + | Y axis : Source IP wise traffic events count |
|- | |- | ||
| − | |Destination IP wise Hits | + | |Destination IP wise Hits |
|X axis : All Source IP in blocked external source traffic <br/> | |X axis : All Source IP in blocked external source traffic <br/> | ||
| − | Y axis : Destination IP wise | + | Y axis : Destination IP wise traffic events count |
|- | |- | ||
|Daily trend | |Daily trend | ||
| Line 323: | Line 380: | ||
|} | |} | ||
| − | ==== | + | ==== Suggestions for useful interaction with this dashboard could be : ==== |
| + | |||
| + | #Click on and select a particular service from Contribution of Services pie chart. The rest of the visualization reflects all Source IP,Destination IP,Protocol etc info with respect to selected Service. | ||
| + | #For further granular detection click on and select particular Source IP or Destination IP from Source IP wise Hits and Destination IP wise Hits bar res. Now rest of the dashboard reflects accordingly. | ||
| − | + | === Checkpoint Firewall Object Manipulation Dashboard=== | |
| − | |||
| − | + | Go to "Dashboards" from the left menu. From the list of in-built dashboards, select this one. It shall open the Dashboard. This dashboard is an User activities audit. It shows the activities performed on the firewall, like creating, modifying and deleting objects. It shows the different types of objects and its table name.You can filter and search information and create new visualizations too. | |
| − | + | For help with Dashboards, click [[KHIKA Dashboards|here]] | |
| − | |||
==== Elements in the Dashboard are explained below : ==== | ==== Elements in the Dashboard are explained below : ==== | ||
{| class="wikitable" | {| class="wikitable" | ||
| − | |+ style="caption-side:bottom; color:#e76700;"|''Elements in " | + | |+ style="caption-side:bottom; color:#e76700;"|''Elements in "Checkpoint Firewall Object Manipulation" Dashboard'' |
|- | |- | ||
|'''Visualization''' | |'''Visualization''' | ||
|'''Description''' | |'''Description''' | ||
|- | |- | ||
| − | |Contribution of | + | |Contribution of Client IP |
| − | |Contribution of | + | |Contribution of Client IP in Object Manipulation Events |
|- | |- | ||
| − | |Contribution of Object Name | + | |Contribution of Object Name |
|Contribution of Object Name in Object Manipulation Events | |Contribution of Object Name in Object Manipulation Events | ||
|- | |- | ||
| − | |Contribution of Object Type | + | |Contribution of Object Type |
|Contribution of Object Type in Object Manipulation Events | |Contribution of Object Type in Object Manipulation Events | ||
|- | |- | ||
| − | |Administrator wise Operation | + | |Administrator wise Operation |
|X axis : All Administrator user in Object Manipulation <br/> | |X axis : All Administrator user in Object Manipulation <br/> | ||
Y axis : Stacked within each bar (ie. for each operation) the Administrator and count of events | Y axis : Stacked within each bar (ie. for each operation) the Administrator and count of events | ||
| Line 362: | Line 420: | ||
|} | |} | ||
| + | ==== Suggestions for useful interaction with this dashboard could be : ==== | ||
| − | + | #Click on and select a particular object type from Contribution of Object Type pie chart. The rest of the visualizations reflect Object Names,Client IPs,Operation etc info with respect to selected object type. | |
| − | + | #For further drill down click on and select particular Administrator user from Operation wise bar chart. It shows operations like modify rule,create object,modify object for that Administrator user. | |
| − | #Click on and select a particular object type from Contribution of Object Type pie. The rest of the | ||
| − | #For further drill down click on and select particular Administrator user from Operation wise bar . | ||
| − | |||
| − | |||
=== Chekpoint Firewall Alerts === | === Chekpoint Firewall Alerts === | ||
| − | + | Alerts are generated when certain critical behavior is observed in the system. Alerts can be monitored in real-time on Alerts Dashboard in KHIKA. Relevant stakeholders can also receive the alerts via emails. The table below explains all the pre-canned alerts shipped with KHIKA App for Checkpoint Firewall. | |
| − | Alerts are generated when certain critical behavior is observed in the system | ||
| − | |||
| − | |||
| − | |||
==== Alerts Description ==== | ==== Alerts Description ==== | ||
| Line 387: | Line 438: | ||
|'''Suggested Resolution''' | |'''Suggested Resolution''' | ||
|- | |- | ||
| − | |Checkpoint firewall Possible data | + | |Checkpoint firewall Possible data Exfiltration |
| − | |This alert is triggered when large amount of data (more than 5 MB ) being sent to an external network. | + | |This alert is triggered when large amount of data (more than 5 MB ) is being sent to an external network. |
|This alert is detected when a large amount of data is uploaded on external sites. This may be an attempt of data ex-filtration from the organisation. | |This alert is detected when a large amount of data is uploaded on external sites. This may be an attempt of data ex-filtration from the organisation. | ||
Please check the real user associated with the source IP and the workstation from which the data upload happened. Verify if sensitive data was ex-filtrated. | Please check the real user associated with the source IP and the workstation from which the data upload happened. Verify if sensitive data was ex-filtrated. | ||
|- | |- | ||
|Checkpoint firewall Checkpoint control log message | |Checkpoint firewall Checkpoint control log message | ||
| − | |This alert is triggered when action is | + | |This alert is triggered when action is ctl and an internal message is generated by Checkpoint Firewall |
| − | |Checkpoint internal message is generated. Please check the documentation of Checkpoint and do the suggested action. | + | |Checkpoint Firewall internal message is generated. Please check the documentation of Checkpoint and do the suggested action. |
|- | |- | ||
|Checkpoint firewall Possible icmp probe | |Checkpoint firewall Possible icmp probe | ||
| − | |This alert is triggered when high inbound icmp | + | |This alert is triggered when high inbound icmp requests are made and are accepted |
|ICMP probe is an old and established technique used by attackers as the first step that involves reconnaissance. This is used to check what IPs/Hosts are responding to the ping request so that further targeted can be launched on the responding IPs/Hots.<br/><br/> | |ICMP probe is an old and established technique used by attackers as the first step that involves reconnaissance. This is used to check what IPs/Hosts are responding to the ping request so that further targeted can be launched on the responding IPs/Hots.<br/><br/> | ||
The probing IP, if not a legitimate IP, ,it should be blocked at the periphery. | The probing IP, if not a legitimate IP, ,it should be blocked at the periphery. | ||
| Line 403: | Line 454: | ||
|- | |- | ||
|Checkpoint firewall IPS bypassing | |Checkpoint firewall IPS bypassing | ||
| − | |This alert is triggered when | + | |This alert is triggered when IPS is bypassed. |
|The firewall IPS mode is enabled by default in NextGen firewalls. However, sometimes the firewall runs out of its resources, such as CPU or Memory due sudden heavy load. In such cases, the firewall disables the IPS mode so that it can service the traffic traffic. Disabled IPS mode on the peripheral firewall is a compromised operating mode as an attacker can invade into your network by exploiting the lack of IPS service on your firewall. | |The firewall IPS mode is enabled by default in NextGen firewalls. However, sometimes the firewall runs out of its resources, such as CPU or Memory due sudden heavy load. In such cases, the firewall disables the IPS mode so that it can service the traffic traffic. Disabled IPS mode on the peripheral firewall is a compromised operating mode as an attacker can invade into your network by exploiting the lack of IPS service on your firewall. | ||
|- | |- | ||
|Checkpoint firewall Worm detected | |Checkpoint firewall Worm detected | ||
| − | |This alert is triggered when traffic is generated on port 445,137,138,139 and | + | |This alert is triggered when traffic is generated on port 445,137,138,139 and communication direction is inbound |
|Log messages indicative of a worm are detected. Check the attacking IPs in question. Verify the reputation these IPs in reputation databased such as virustotal.com, ipvoid.com etc. | |Log messages indicative of a worm are detected. Check the attacking IPs in question. Verify the reputation these IPs in reputation databased such as virustotal.com, ipvoid.com etc. | ||
|- | |- | ||
| Line 420: | Line 471: | ||
|- | |- | ||
|Checkpoint firewall Communication with possible IOC or bad IP | |Checkpoint firewall Communication with possible IOC or bad IP | ||
| − | |This alert is triggered when | + | |This alert is triggered when any one of the Source or Destination IP is found malicious with accepted action |
|KHIKA shares community based threat intelligence (TI) every 24 hours. TI has list of IP addresses with bad reputation. Every bad IP is marked with number of communities reporting it, name of each community and confidence indicating how confident are we about the reputation. This alert is generated when communication with a bad IP is let through.<br/><br/> | |KHIKA shares community based threat intelligence (TI) every 24 hours. TI has list of IP addresses with bad reputation. Every bad IP is marked with number of communities reporting it, name of each community and confidence indicating how confident are we about the reputation. This alert is generated when communication with a bad IP is let through.<br/><br/> | ||
If communication with a bad IP is happening, it must be blocked immediately as it could be a possible attack or data ex-filtration. | If communication with a bad IP is happening, it must be blocked immediately as it could be a possible attack or data ex-filtration. | ||
| Line 428: | Line 479: | ||
It is critical to block this rogue communication. | It is critical to block this rogue communication. | ||
|- | |- | ||
| − | |Checkpoint firewall host scan activity by malicious | + | |Checkpoint firewall host scan activity by malicious IP |
| − | |This alert is triggered when same | + | |This alert is triggered when same malicious ip is trying to generate traffic for one destination ip on more than 10 different ports within 1 minute and the request is denied. |
|Bad ip address tries to spray connection requests on multiple popular ports (21,22,53,80,443 etc) targeting one single IP address at a time with an intention to find the open ports on the target IP address. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle.<br/><br/> | |Bad ip address tries to spray connection requests on multiple popular ports (21,22,53,80,443 etc) targeting one single IP address at a time with an intention to find the open ports on the target IP address. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle.<br/><br/> | ||
It is important to check the reputation of the external ip address and block the same if necessary. | It is important to check the reputation of the external ip address and block the same if necessary. | ||
|- | |- | ||
|Checkpoint firewall successful host scan activity | |Checkpoint firewall successful host scan activity | ||
| − | |This alert is triggered when same source ip is trying to generate traffic | + | |This alert is triggered when same source ip is trying to generate traffic for one destination ip on more than 10 different ports but all the time request is denied .After that same source IP attempts to connect to same destination on one more port and this time it successfully connects on that port. All this happen within 1 minute. |
|Attacker tries to spray connection requests on multiple popular ports (21,22,53,80,443 etc) targeting one single IP addresses at a time with an intention to find the open ports on the target IP address. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle and attacker done successful connection on open ports<br/><br> | |Attacker tries to spray connection requests on multiple popular ports (21,22,53,80,443 etc) targeting one single IP addresses at a time with an intention to find the open ports on the target IP address. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle and attacker done successful connection on open ports<br/><br> | ||
| − | It is important to check the reputation of the suspected | + | It is important to check the reputation of the suspected IP address. |
| − | If the suspected | + | If the suspected IP address is external, you may consider blocking it. |
| − | If the suspected | + | If the suspected IP address is internal, you may need to verify the sanity of the corresponding device |
It is also important to verify the sanity of affected internal nodes by checking if any unwarranted system policy change or software configuration/updates have occurred during the affected time period. If required, quarantine the affected servers till the time the issues are resolved. | It is also important to verify the sanity of affected internal nodes by checking if any unwarranted system policy change or software configuration/updates have occurred during the affected time period. If required, quarantine the affected servers till the time the issues are resolved. | ||
This may be a false positive. | This may be a false positive. | ||
|- | |- | ||
| − | |Checkpoint firewall successful host scan activity by malicious | + | |Checkpoint firewall successful host scan activity by malicious IP |
| − | |This alert is triggered when same | + | |This alert is triggered when same malicious IP is trying to generate traffic for one destination IP on more than 10 different ports, but all the time request is denied .After that same malicious IP attempt to connect to same destination IP on one more port and this time it successfully connected on that port. All this happen within 1 minute. |
| − | |Bad | + | |Bad IP address tries to spray connection requests on multiple popular ports (21,22,53,80,443 etc) targeting one single IP addresses at a time with an intention to find the open ports on the target IP address. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle and attacker done successful connection on open ports<br/></br> |
| − | It is important to check the reputation of the external | + | It is important to check the reputation of the external IP address and block the same if necessary. |
It is also important to verify the sanity of affected internal nodes by checking if any unwarranted system policy change or software configuration/updates have occurred during the affected time period. If required, quarantine the affected servers till the time the issues are resolved. | It is also important to verify the sanity of affected internal nodes by checking if any unwarranted system policy change or software configuration/updates have occurred during the affected time period. If required, quarantine the affected servers till the time the issues are resolved. | ||
|- | |- | ||
| − | |Checkpoint firewall sweep scan attack by malicious | + | |Checkpoint firewall sweep scan attack by malicious IP |
| − | |This alert is triggered when same | + | |This alert is triggered when same malicious IP is trying to generate traffic on more than 10 destination ip but all the time request is denied . All this happens within 1 minute. |
|Attacker tries to spray connection requests on one of the popular ports (21,22,53,80,443 etc) on multiple IP addresses with an intention to find which ports are opened on what IP addresses. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle and attacker done successful connection | |Attacker tries to spray connection requests on one of the popular ports (21,22,53,80,443 etc) on multiple IP addresses with an intention to find which ports are opened on what IP addresses. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle and attacker done successful connection | ||
| − | Bad | + | Bad IP addresses tries to spray connection requests on one of the popular ports (21,22,53,80,443 etc) on multiple IP addresses with an intention to find which ports are opened on what IP addresses. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle.<br/><br/> |
It is important to check the reputation of the external ip address and block the same if necessary. | It is important to check the reputation of the external ip address and block the same if necessary. | ||
|- | |- | ||
|Checkpoint firewall successful sweep scan activity | |Checkpoint firewall successful sweep scan activity | ||
| − | |This alert is triggered when same source | + | |This alert is triggered when same source IP is trying to generate traffic on more than 10 destination ip but all the time request is denied .After that same source IP attempts to connect one more destination IP and this time it successfully connects. All this happen within 1 minute. |
| − | |Attacker tries to spray connection requests on one of the popular ports (21,22,53,80,443 etc) on multiple IP addresses with an intention to find which ports are opened on what IP addresses. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle and attacker done successful connection on one of | + | |Attacker tries to spray connection requests on one of the popular ports (21,22,53,80,443 etc) on multiple IP addresses with an intention to find which ports are opened on what IP addresses. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle and attacker done successful connection on one of IP addresses |
| − | It is important to check the reputation of the suspected | + | It is important to check the reputation of the suspected IP address. |
| − | If the suspected | + | If the suspected IP address is external, you may consider blocking it. |
| − | If the suspected | + | If the suspected IP address is internal, you may need to verify the sanity of the corresponding device |
It is also important to verify the sanity of affected internal nodes by checking if any unwarranted system policy change or software configuration/updates have occurred during the affected time period. If required, quarantine the affected servers till the time the issues are resolved. | It is also important to verify the sanity of affected internal nodes by checking if any unwarranted system policy change or software configuration/updates have occurred during the affected time period. If required, quarantine the affected servers till the time the issues are resolved. | ||
This may be a false positive. | This may be a false positive. | ||
|- | |- | ||
| − | |Checkpoint firewall successful sweep scan activity by malicious | + | |Checkpoint firewall successful sweep scan activity by malicious IP |
| − | |This alert is triggered when same | + | |This alert is triggered when same malicious IP is trying to generate traffic on more than 10 destination IP but all the time request is denied .After that same source IP attempts to connect to one more destination IP and this time it successfully connects. All this happen within 1 minute. |
| − | |Bad | + | |Bad Ip address tries to spray connection requests on one of the popular ports (21,22,53,80,443 etc) on multiple IP addresses with an intention to find which ports are opened on what IP addresses. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle and attacker finds open port on one of IP addresses and is able to establish a connection. |
| − | It is important to check the reputation of the external | + | It is important to check the reputation of the external IP address and block the same if necessary. |
It is also important to verify the sanity of affected internal nodes by checking if any unwarranted system policy change or software configuration/updates have occurred during the affected time period. If required, quarantine the affected servers till the time the issues are resolved. | It is also important to verify the sanity of affected internal nodes by checking if any unwarranted system policy change or software configuration/updates have occurred during the affected time period. If required, quarantine the affected servers till the time the issues are resolved. | ||
|- | |- | ||
| − | |Checkpoint firewall communication with suspicious | + | |Checkpoint firewall communication with suspicious IP |
| − | |This alert is triggered when bytes are sent and received during communication with malicious | + | |This alert is triggered when bytes are sent and received during communication with malicious IP within 1 minute. |
|Communication with a bad IP is happening, it must be blocked immediately as it could be a possible attack or data ex-filtration. | |Communication with a bad IP is happening, it must be blocked immediately as it could be a possible attack or data ex-filtration. | ||
You can check the log for this communication by simply searching the malicious IP in the logs. You can also check which internal IP addresses are communicating with this IP address and track the real users behind those internal IP addresses.<br/><br/> | You can check the log for this communication by simply searching the malicious IP in the logs. You can also check which internal IP addresses are communicating with this IP address and track the real users behind those internal IP addresses.<br/><br/> | ||
Latest revision as of 07:47, 30 July 2019
Contents
- 1 Introduction
- 2 Enabling Syslog forwarding on the device
- 3 Verifying SYSLOG data collection
- 4 How to Install the KHIKA App for Checkpoint Firewall ?
- 5 Adding the device in the Adaptor
- 6 How to check the output of KHIKA Checkpoint Firewall App ?
- 6.1 Discovering the logs of Checkpoint Firewall
- 6.2 Checkpoint Firewall Malicious Communication Dashboard
- 6.3 Checkpoint Firewall Triggered Signature Dashboard
- 6.4 Chekpoint Firewall VPN Activity Dashboard
- 6.5 Checkpoint Firewall Attack Dashboard
- 6.6 Checkpoint Firewall Audit Admin login Dashboard
- 6.7 Checkpoint Firewall Allowed External Source Dashboard
- 6.8 Checkpoint Firewall Blocked External Source Dashboard
- 6.9 Checkpoint Firewall Object Manipulation Dashboard
- 6.10 Chekpoint Firewall Alerts
Introduction
Firewalls are used to control the peripheral traffic and communication in organisations and hence its essential and critical to monitor them. Checkpoint Firewall sends the traffic and user activity related information in the form of logs over syslog protocol. KHIKA Data Aggregator is pre-configured with syslog services on port 514.
The key parts to get here are :
- Enabling Syslog forwarding on the firewall device
- Install the KHIKA App for Checkpoint Firewall
- Get data from your Checkpoint Firewall into the KHIKA Aggregator
Enabling Syslog forwarding on the device
Please refer here for enabling syslogs on your Checkpoint firewall device.
Example of a command to be fired on Firewall Device to enable syslogs:
cp_log_export add name <name> [domain-server <domain-server>] target-server <target-server IP address> target-port <target-port> protocol <(udp|tcp)> format <(syslog)|(cef)|(splunk)(generic)>
name :Unique name of the exporter configuration. domain-server :The relevant domain-server name or IP target-server :Exporting the logs to this ip address target-port :The port on which the target is listening to.Here use port 514 protocol :Transport protocol to use.Here use protocol udp format :The format in which the logs will be exported .Here use format cef
Verifying SYSLOG data collection
After you enable the syslog forwarding on the end device, you must verify if the logs are being really received by KHIKA Data Aggregator. Please refer here to understand how to verify syslogs on KHIKA Data Aggregator.
How to Install the KHIKA App for Checkpoint Firewall ?
It is assumed, that you have already configured KHIKA Data Aggregator in your environment. If not, please read how to configure KHIKA Data Aggregator and perform the pre-requisite steps.
This section explains how to pick and install the KHIKA application for Checkpoint Firewall. Installing the application shall put together and activate the adapter (parser) that can handle Checkpoint Firewall data format, the dashboards and the alert rules preconfigured.
Go to “Applications” tab in the “Configure” menu.
Check whether the appropriate Workspace is selected. Note: Application is always loaded in a Workspace. Read the section on Workspaces to know more about KHIKA Workspaces. Also select your KHIKA aggregator name in the Node dropdown. This is to ensure that we are collecting data from the desired source and into the correct workspace which is ready with the configured application and components.
Click on the “+” button next to the Checkpoint Firewall App. A pop up appears.
User can now select the contents of the application required. For example, on the dropdown for “Reports”, click to expand it. List of all reports can be seen. User can individually select the reports required by checking on the checkbox next to each. Alternatively, check on “Select All” option to get all of them. Similarly you can select contents from Alerts and Dashboards.
Visit the sections on KHIKA Reports, KHIKA Dashboards, KHIKA Alerts & Correlations to know more about these topics.
Click “OK” to proceed with the installation of the selected Application. After successful installation, following status should be displayed :
This simple procedure to install a KHIKA App, automatically configures the Adapter (required for parsing the data from raw syslogs), calculated KHIKA reports on raw data, Visualizations, Dashboards and Alerts – all in one click.
Adding the device in the Adaptor
After syslogs are enabled on the device and the App is installed into KHIKA, it is the time to add the device to the this App (in Adapter section of KHIKA Web GUI). Please refer here to know how to add the device to an App.
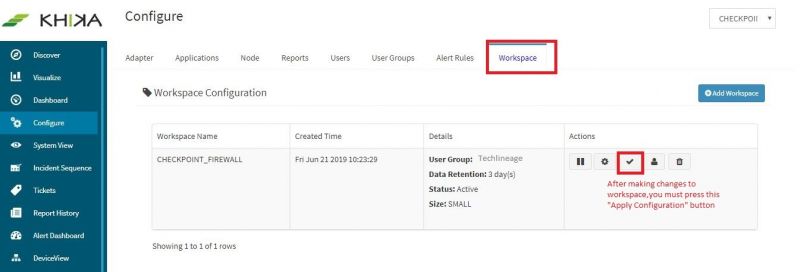
After making these configuration in KHIKA, you must apply these changes to the Workspace. Go to Configure, select the Workspace and in Workspace tab of configure menu press the Apply button as shown in the screenshot below.
Wait for a few minutes for changes to apply and data to arrive in kHIKA. With all these steps, we should now expect the data to arrive in KHIKA. Lets discover some live data in KHIKA.
How to check the output of KHIKA Checkpoint Firewall App ?
Discovering the logs of Checkpoint Firewall
After doing all the steps given above, we should start receiving live data into KHIKA. Go to "Discover" section in KHIKA GUI and select the index with name "*raw-checkpoint_firewall*". Note that the index has a prefix of the customer name and workspace name. After selecting this index, you should see the live data coming in. Spend some time understanding this data and the fields of the data.
Checkpoint Firewall Malicious Communication Dashboard
Go to "Dashboards" from the left menu. From the list of in-built dashboards, select this one. It shall open the Dashboard.
This dashboard focuses on the Checkpoint Firewall communication with suspicious IP addresses and it's traffic status(which is added into KHIKA).Details like the malicious IP address,the source IP and destination IP at that time, actions, service, traffic direction etc. is shown in an analytical fashion. You can filter and search information and create new visualizations ones too.
For help with Dashboards, click here
Elements in the Dashboard are explained below :
| Visualization | Description |
| Contribution of Action | Contribution of actions during communication with malicious IPs |
| Contribution of Malicious IP | Contribution of Malicious IP addresses, according to no. of events occured in logs. |
| Malicious IP wise Action | X axis : All Malicious IPs communicated through the firewall Y axis : Actions stacked in one bar(Malicious IP) and their count |
| Source IP wise Hits | X axis : Source IPs found in Malicious Communication Y axis : The count of Source IPs during Malicious Communication |
| Destination IP wise Hits | X axis : Destination IPs found in Malicious Communication Y axis : The count of Destination IP during Malicious Communication |
| Daily trend | Trend of malicious communication events over time. Useful to identify unusual spikes at a glance. X axis : date & time Y axis : count of events |
| Summary Table | Detailed data with timestamp and count |
Suggestions for useful interaction with this dashboard could be :
- Select a particular malicious IP from the Contribution of Malicious IP pie. Rest of the visualizations reflect all source IP, destination IP and actions with respect to this malicious IP.
- Select an action from Contribution of Action pie. You can check what traffic gets accepted and wether it is from any particular source or unusually high at any time of the day and so on.
Checkpoint Firewall Triggered Signature Dashboard
Go to "Dashboards" from the left menu. From the list of in-built dashboards, select this one. It shall open the Dashboard.
This dashboard gives attack information against predefined signatures of attacks. It includes information about source and destination IPs and also possible malicious IPs among them. What action has been taken by firewall on each is also present. You can filter and search information and create new visualizations too.
For help with Dashboards, click here
Elements in the Dashboard are explained below :
| Visualization | Description |
| Contribution of Action | Contribution of Actions in signatures of attacks |
| Contribution of Attack | Contribution of Attacks according to no. of events occured |
| Source IP wise Attack Hits | X axis : Source IPs found during Attack Y axis : Stacked within each bar (ie. for each Attack) the Source IP and count of events |
| Destination IP wise Attack Hits | X axis : All the Source IPs during Signature Attack Y axis : Stacked within each bar (ie. for each Attack) the Destination IP and count of events |
| Daily trend | Trend of attack events over time. Useful to identify unusual spikes at a glance. X axis : date & time Y axis : count of events |
| Summary Table | Detailed data with timestamp and count |
Suggestions for useful interaction with this dashboard could be :
- Click on or select a particular attack in the Contribution of Attack pie. The rest of the dashboard reflects all source IPs,destination IPs and actions with respect to selected attack.
- For more granular detection select particular action from Contribution of Action pie chart, now rest of the dashboard will reflect accordingly.
Chekpoint Firewall VPN Activity Dashboard
Go to "Dashboards" from the left menu. From the list of in-built dashboards, select this one. It shall open the Dashboard.
This dashboard gives Checkpoint Firewall VPN activity details like Source IP, Destination IP, VPN user, Interface Name, Policy Name, Interface Direction etc. in analytical fashion. You can filter and search information and create new ones too. For help with Dashboards, click here
Elements in the Dashboard are explained below :
| Visualization | Description |
| Contribution of VPN User pie chart | Contribution of VPN User according to no. of events occured |
| Contribution of Action pie chart | Contribution of Actions taken on VPN traffic |
| Source IP wise Hits | X axis : Source IPs found during VPN Activity Y axis : The count of Source IPs during VPN |
| Destination IP wise Hits | X axis : All the Source IPs during VPN Activityk Y axis : The count of Destination IP during VPN |
| Contribution of Protocol pie chart | Contribution of Protocol during VPN |
| Contribution of Policies | Contribution of Policies during VPN |
| Daily trend | Trend of VPN activity events over time. Useful to identify unusual spikes at a glance. X axis : date & time Y axis : count of events |
| Summary Table | Detailed data with timestamp and count |
A suggestion for useful interaction with this dashboard could be :
- Click on and select a particular user in the Contribution of User pie. The rest of the visualization reflects all source IPs,destination IPs,policies,actions etc. with respect to selected VPN user.
- Click on and select particular action in the Contribution of Action pie. Now rest of the visualizations will reflect accordingly.
Checkpoint Firewall Attack Dashboard
Go to "Dashboards" from the left menu. From the list of in-built dashboards, select this one. It shall open the Dashboard.
This dashboard gives Checkpoint Firewall attack information. You can filter and search information and create new visualizations too.
For help with Dashboards, click here
Elements in the Dashboard are explained below :
| Visualization | Description |
| Contribution of Attack | Contribution of Attacks according to the occurence |
| Contribution of Malicious IP | Contribution of Malicious IPs in Attack events |
| Attack wise Attack Info | X axis : Attacks accross Firewall Y axis : Stacked within each bar (ie. for each Attack info) the Attack Name and count of events |
| Source IP wise Attack | X axis : Source IPs found during Signature Attack Y axis : Stacked within each bar (ie. for each Attack) the Source IP and count of events |
| Destination IP wise Attack | X axis : All the Source IP during Signature Attack Y axis : Stacked within each bar (ie. for each Attack) the Destination IP and count of events |
| Daily trend | Trend of Attack events over time. Useful to identify unusual spikes at a glance. X axis : date & time Y axis : count of events |
| Summary Table | Detailed data with timestamp and count |
Suggestions for useful interaction with this dashboard could be :
- Click on and select a particular attack from contribution of attack pie chart. The rest of the visualization reflects information like source IP,destination IP and attack info with respect to selected Attack.
- Select particular source IP in the Source wise attack bar chart. Now rest of the visualizations will reflect accordingly.
Checkpoint Firewall Audit Admin login Dashboard
Go to "Dashboards" from the left menu. From the list of dashboards, select this one. It shall open the Dashboard. This shows Checkpoint Firewall login information. It shows status of logins, from where user has logged in, which product is used for login (product like smart dashboard,smart view tracker, smart view monitor etc). You can filter and search information and create new visualizations too.
For help with Dashboards, click here
Elements in the Dashboard are explained below :
| Visualization | Description |
| Contribution of Status | Contribution of status like success,failure etc in admin user login events |
| Contribution of Machine | Machine Name from where admin user was trying to login |
| Admin user wise Status: | X axis : Admin users who have login into Firewall Y axis : Admin users wise login failed and success status and its count |
| Client IP wise Operation | X axis : All client IP in login activity Y axis : Stacked within each bar (ie. for each operation like log in etc) the Client IP and count of events |
| Daily trend | Trend of Admin login events over time. Useful to identify unusual spikes at a glance. X axis : date & time Y axis : count of events |
| Summary Table | Detailed data with timestamp and count |
Suggestions for useful interaction with this dashboard could be :
- Click on and select a particular status from contribution of Status pie. The rest of the visualization reflects for all Admin users the Machine Names and Client Names for selected status
- Select particular Admin user in Admin wise status bar. Now rest of the visualizations will reflect accordingly.
Checkpoint Firewall Allowed External Source Dashboard
Go to "Dashboards" from the left menu. From the list of in-built dashboards, select this one. It shall open the Dashboard. This dashboard shows traffic which the Checkpoint Firewall allowed from external sources. Here traffic origin is external and is accepted by firewall. This dashboard gives you a control over all the external incoming traffic through your peripheral firewall.
You can filter and search information and create new visualizations too.
For help with Dashboards, click here
Elements in the Dashboard are explained below :
| Visualization | Description |
| Contribution of Protocol | Contribution Protocol in allowed traffic from external sources |
| Contribution of Services | Contribution of Services in allowed traffic from external sources |
| Source IP wise Hits | X axis : All Source IP found in allowed traffic from external sources Y axis : Source IP wise events count |
| Destination IP wise Hits | X axis : All Source IP in allowed traffic from external sources Y axis : Destination IP wise events count |
| Daily trend | Trend of allowed external traffic events over time. Useful to identify unusual spikes at a glance. X axis : date & time Y axis : count of events |
| Summary Table | Detailed data with timestamp and count |
Suggestions for useful interaction with this dashboard could be :
- Click on and select a particular service from Contribution of Services pie chart. The rest of the visualization reflects all Source IP,Destination IP,Protocol etc info with respect to selected service.
- For further granular detection click on and select particular Source IP or Destination IP from Source IP wise Hits and Destination IP wise Hits bar chart res.Now rest of the visualization will reflect accordingly.
Checkpoint Firewall Blocked External Source Dashboard
Go to "Dashboards" from the left menu. From the list of dashboards, select this one. It shall open the Dashboard. This dashboard shows traffic blocked by the Checkpoint Firewall from external sources. Here traffic origin is external and this traffic is blocked by the firewall. You can filter and search information and create new ones too. For help with Dashboards, click here
Elements in the Dashboard are explained below :
| Visualization | Description |
| Contribution of Protocol | Contribution Protocol in blocked traffic from external sources |
| Contribution of Services | Contribution of Services in blocked traffic from external sources |
| Source IP wise Hits | X axis : All Source IP in blocked external source traffic Y axis : Source IP wise traffic events count |
| Destination IP wise Hits | X axis : All Source IP in blocked external source traffic Y axis : Destination IP wise traffic events count |
| Daily trend | Trend of blocked external traffic events over time. Useful to identify unusual spikes at a glance. X axis : date & time Y axis : count of events |
| Summary Table | Detailed data with timestamp and count |
Suggestions for useful interaction with this dashboard could be :
- Click on and select a particular service from Contribution of Services pie chart. The rest of the visualization reflects all Source IP,Destination IP,Protocol etc info with respect to selected Service.
- For further granular detection click on and select particular Source IP or Destination IP from Source IP wise Hits and Destination IP wise Hits bar res. Now rest of the dashboard reflects accordingly.
Checkpoint Firewall Object Manipulation Dashboard
Go to "Dashboards" from the left menu. From the list of in-built dashboards, select this one. It shall open the Dashboard. This dashboard is an User activities audit. It shows the activities performed on the firewall, like creating, modifying and deleting objects. It shows the different types of objects and its table name.You can filter and search information and create new visualizations too.
For help with Dashboards, click here
Elements in the Dashboard are explained below :
| Visualization | Description |
| Contribution of Client IP | Contribution of Client IP in Object Manipulation Events |
| Contribution of Object Name | Contribution of Object Name in Object Manipulation Events |
| Contribution of Object Type | Contribution of Object Type in Object Manipulation Events |
| Administrator wise Operation | X axis : All Administrator user in Object Manipulation Y axis : Stacked within each bar (ie. for each operation) the Administrator and count of events |
| Daily trend | Trend of object manipulation events over time. Useful to identify unusual spikes at a glance. X axis : date & time Y axis : count of events |
| Summary Table | Detailed data with timestamp and count |
Suggestions for useful interaction with this dashboard could be :
- Click on and select a particular object type from Contribution of Object Type pie chart. The rest of the visualizations reflect Object Names,Client IPs,Operation etc info with respect to selected object type.
- For further drill down click on and select particular Administrator user from Operation wise bar chart. It shows operations like modify rule,create object,modify object for that Administrator user.
Chekpoint Firewall Alerts
Alerts are generated when certain critical behavior is observed in the system. Alerts can be monitored in real-time on Alerts Dashboard in KHIKA. Relevant stakeholders can also receive the alerts via emails. The table below explains all the pre-canned alerts shipped with KHIKA App for Checkpoint Firewall.
Alerts Description
| Alert Name | Description | Suggested Resolution |
| Checkpoint firewall Possible data Exfiltration | This alert is triggered when large amount of data (more than 5 MB ) is being sent to an external network. | This alert is detected when a large amount of data is uploaded on external sites. This may be an attempt of data ex-filtration from the organisation.
Please check the real user associated with the source IP and the workstation from which the data upload happened. Verify if sensitive data was ex-filtrated. |
| Checkpoint firewall Checkpoint control log message | This alert is triggered when action is ctl and an internal message is generated by Checkpoint Firewall | Checkpoint Firewall internal message is generated. Please check the documentation of Checkpoint and do the suggested action. |
| Checkpoint firewall Possible icmp probe | This alert is triggered when high inbound icmp requests are made and are accepted | ICMP probe is an old and established technique used by attackers as the first step that involves reconnaissance. This is used to check what IPs/Hosts are responding to the ping request so that further targeted can be launched on the responding IPs/Hots. The probing IP, if not a legitimate IP, ,it should be blocked at the periphery. Check the reputation of the probing IP in external reputation databases, such as VirtusTotal.com or IPVoid.com etc. If the reputation is found to be dubious or bad, you must block such IPs. |
| Checkpoint firewall IPS bypassing | This alert is triggered when IPS is bypassed. | The firewall IPS mode is enabled by default in NextGen firewalls. However, sometimes the firewall runs out of its resources, such as CPU or Memory due sudden heavy load. In such cases, the firewall disables the IPS mode so that it can service the traffic traffic. Disabled IPS mode on the peripheral firewall is a compromised operating mode as an attacker can invade into your network by exploiting the lack of IPS service on your firewall. |
| Checkpoint firewall Worm detected | This alert is triggered when traffic is generated on port 445,137,138,139 and communication direction is inbound | Log messages indicative of a worm are detected. Check the attacking IPs in question. Verify the reputation these IPs in reputation databased such as virustotal.com, ipvoid.com etc. |
| Checkpoint firewall Backdoor activity detected | This alert is triggered when traffic is generated from internal machine on vulnerable ports(3127,3198,6129,7080). | This event indicates that a traffic is generated from internal machine on vulnerable ports(3127,3198,6129,7080). Typically, these ports are used by attacker to exploit vulnerable programs listening on these ports. Check is these ports are open and on what servers. Do you really need these ports opened? Check what programs are running on these ports. Check vulnerability reports of the applications Block these ports for external traffic, unless mandatory to keep them opened. If you have to keep any of these ports opened, try to restrict the access to legitimate IPs. If you get a suspicious IP repetitively trying to access these port, block the IP. Check the reputation of the IP on popular website such as ipvoid.com, virustotal.com etc. |
| Checkpoint firewall Communication with possible IOC or bad IP | This alert is triggered when any one of the Source or Destination IP is found malicious with accepted action | KHIKA shares community based threat intelligence (TI) every 24 hours. TI has list of IP addresses with bad reputation. Every bad IP is marked with number of communities reporting it, name of each community and confidence indicating how confident are we about the reputation. This alert is generated when communication with a bad IP is let through. If communication with a bad IP is happening, it must be blocked immediately as it could be a possible attack or data ex-filtration. You can check how log this communication is happening by simply searching the malicious IP in the logs. You can also check what internal IP addresses are communicating with this IP addresses and track the real users behind those internal IP addresses. Cross-check the reputation of the IP with popular websites such as ipvoid.com, virustotal.com If you see an internal IP constantly getting involved in malicious communication (with same or multiple external IP addresses), you may install agents on the internal nodes involved and check the real user and process responsible for this communication. It is critical to block this rogue communication. |
| Checkpoint firewall host scan activity by malicious IP | This alert is triggered when same malicious ip is trying to generate traffic for one destination ip on more than 10 different ports within 1 minute and the request is denied. | Bad ip address tries to spray connection requests on multiple popular ports (21,22,53,80,443 etc) targeting one single IP address at a time with an intention to find the open ports on the target IP address. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle. It is important to check the reputation of the external ip address and block the same if necessary. |
| Checkpoint firewall successful host scan activity | This alert is triggered when same source ip is trying to generate traffic for one destination ip on more than 10 different ports but all the time request is denied .After that same source IP attempts to connect to same destination on one more port and this time it successfully connects on that port. All this happen within 1 minute. | Attacker tries to spray connection requests on multiple popular ports (21,22,53,80,443 etc) targeting one single IP addresses at a time with an intention to find the open ports on the target IP address. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle and attacker done successful connection on open ports It is important to check the reputation of the suspected IP address. If the suspected IP address is external, you may consider blocking it. If the suspected IP address is internal, you may need to verify the sanity of the corresponding device It is also important to verify the sanity of affected internal nodes by checking if any unwarranted system policy change or software configuration/updates have occurred during the affected time period. If required, quarantine the affected servers till the time the issues are resolved. This may be a false positive. |
| Checkpoint firewall successful host scan activity by malicious IP | This alert is triggered when same malicious IP is trying to generate traffic for one destination IP on more than 10 different ports, but all the time request is denied .After that same malicious IP attempt to connect to same destination IP on one more port and this time it successfully connected on that port. All this happen within 1 minute. | Bad IP address tries to spray connection requests on multiple popular ports (21,22,53,80,443 etc) targeting one single IP addresses at a time with an intention to find the open ports on the target IP address. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle and attacker done successful connection on open ports It is important to check the reputation of the external IP address and block the same if necessary. It is also important to verify the sanity of affected internal nodes by checking if any unwarranted system policy change or software configuration/updates have occurred during the affected time period. If required, quarantine the affected servers till the time the issues are resolved. |
| Checkpoint firewall sweep scan attack by malicious IP | This alert is triggered when same malicious IP is trying to generate traffic on more than 10 destination ip but all the time request is denied . All this happens within 1 minute. | Attacker tries to spray connection requests on one of the popular ports (21,22,53,80,443 etc) on multiple IP addresses with an intention to find which ports are opened on what IP addresses. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle and attacker done successful connection
Bad IP addresses tries to spray connection requests on one of the popular ports (21,22,53,80,443 etc) on multiple IP addresses with an intention to find which ports are opened on what IP addresses. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle. |
| Checkpoint firewall successful sweep scan activity | This alert is triggered when same source IP is trying to generate traffic on more than 10 destination ip but all the time request is denied .After that same source IP attempts to connect one more destination IP and this time it successfully connects. All this happen within 1 minute. | Attacker tries to spray connection requests on one of the popular ports (21,22,53,80,443 etc) on multiple IP addresses with an intention to find which ports are opened on what IP addresses. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle and attacker done successful connection on one of IP addresses
It is important to check the reputation of the suspected IP address. If the suspected IP address is external, you may consider blocking it. If the suspected IP address is internal, you may need to verify the sanity of the corresponding device It is also important to verify the sanity of affected internal nodes by checking if any unwarranted system policy change or software configuration/updates have occurred during the affected time period. If required, quarantine the affected servers till the time the issues are resolved. This may be a false positive. |
| Checkpoint firewall successful sweep scan activity by malicious IP | This alert is triggered when same malicious IP is trying to generate traffic on more than 10 destination IP but all the time request is denied .After that same source IP attempts to connect to one more destination IP and this time it successfully connects. All this happen within 1 minute. | Bad Ip address tries to spray connection requests on one of the popular ports (21,22,53,80,443 etc) on multiple IP addresses with an intention to find which ports are opened on what IP addresses. Typically, scan attempt is the first stage of reconnaissance in the attack life cycle and attacker finds open port on one of IP addresses and is able to establish a connection.
It is important to check the reputation of the external IP address and block the same if necessary. It is also important to verify the sanity of affected internal nodes by checking if any unwarranted system policy change or software configuration/updates have occurred during the affected time period. If required, quarantine the affected servers till the time the issues are resolved. |
| Checkpoint firewall communication with suspicious IP | This alert is triggered when bytes are sent and received during communication with malicious IP within 1 minute. | Communication with a bad IP is happening, it must be blocked immediately as it could be a possible attack or data ex-filtration.
You can check the log for this communication by simply searching the malicious IP in the logs. You can also check which internal IP addresses are communicating with this IP address and track the real users behind those internal IP addresses. |
| Checkpoint firewall large data sent outside | This alert is triggered when large amount of data (more than 1 GB) being sent to an external network | Large amount of data being sent to an external network could be an indication of data ex-filtration.
Check with the user or process which is responsible for the data being sent out and whether it was done for legitimate business reasons. This could be a false positive.
|