Difference between revisions of "File Integrity Monitoring"
| Line 11: | Line 11: | ||
| − | + | [[File:Fim1.jpg|700px]] | |
| − | + | ||
| + | Below is a sample file Integrity monitoring dashboard | ||
| + | |||
| + | |||
| + | [[File:Fim1.jpg|700px]] | ||
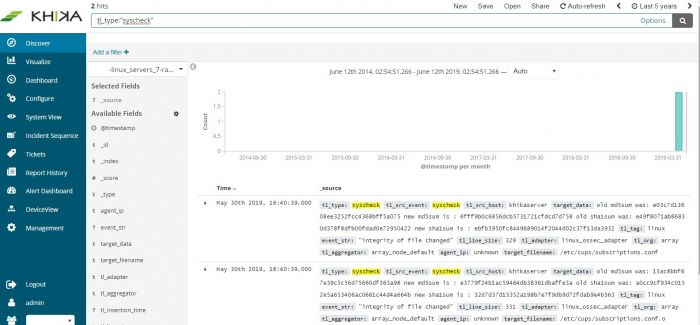
In the column – target data, old md5 and sha1sum values and the current values are shown. When the content of the registry or file change, these values change. Under tl_src_event column, we can see if it is a change in the registry or file. In above example the registry value has changed. | In the column – target data, old md5 and sha1sum values and the current values are shown. When the content of the registry or file change, these values change. Under tl_src_event column, we can see if it is a change in the registry or file. In above example the registry value has changed. | ||
Revision as of 10:13, 12 June 2019
There are multiple types of attacks and many attack vectors, and most of them make some changes in the critical files of the system, thus altering the integrity of the system. The security posture of a computer is changed when a critical file on a computer is changed. Imagine someone with malicious intent changing resolv.conf file on your computer! You will be redirected to unwanted sites when you type your favorite site in the browser. This was just an example to demonstrate why it is so important to monitor changes to critical files on your computers and critical servers.
File Integrity Monitoring or FIM is the process which validates the integrity of the files on the operating system, any change in the crucial files against a standard baseline. It is a service that monitors any changes made to crucial files.
KHIKA uses OSSEC agent on the server to gather logs, critical information about the system and monitor file integrity. Syscheck is the name of the integrity checking process inside OSSEC. It runs periodically to check if any configured file (or registry entry on Windows) has changed. This process runs every 6 hours by default but the frequency or time/day are configurable. Moreover, it can be configured for real-time file integrity monitoring on certain systems (specific versions of Linux and Windows)
KHIKA receives the raw FIM data from ossec and stores it in its repository.
The FIM events can be searched using KHIKA’s search interface - Discover. Below is a sample output of search results of FIM Events in KHIKA
Below is a sample file Integrity monitoring dashboard
In the column – target data, old md5 and sha1sum values and the current values are shown. When the content of the registry or file change, these values change. Under tl_src_event column, we can see if it is a change in the registry or file. In above example the registry value has changed.