Difference between revisions of "KHIKA App for Cisco Switch"
(→How to check the output of KHIKA Sophos Firewall App ?) |
(→Some suggestions for useful interaction with this dashboard could be :) |
||
| (45 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
| − | == How to check the output of | + | == Introduction == |
| + | |||
| + | Most of the network devices, such as firewalls, switches, routers, web proxies etc send the traffic and user activity related information in the form of logs over syslog protocol. Some applications such as Oracle database server, Symantec antivirus server, EMC SAN Storage etc also support syslog protocol as syslog is very efficient and simple to integrate with. KHIKA Data Aggregator is pre-configured with syslog services on port 514. | ||
| + | The key parts to get here are : | ||
| + | #Enabling Syslog forwarding on the device | ||
| + | #Install the KHIKA App for Cisco Switch | ||
| + | #Get data from your Cisco Switch into KHIKA Aggregator | ||
| + | |||
| + | == Enabling Syslog forwarding on the device == | ||
| + | Please refer "Configuring the UNIX System Logging Facility" section in [https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst2960/software/release/12-2_55_se/configuration/guide/scg_2960/swlog.html#Configur Cisco Switch Documentation] for enabling syslogs on your cisco switch device. | ||
| + | |||
| + | Example of commands to be fired on Cisco Switch Device to enable syslogs:</br> | ||
| + | 1. logging <IP Address of khika aggregator></br> | ||
| + | 2. logging trap debugging (7)</br> | ||
| + | 3. logging on</br> | ||
| + | 4. service timestamps log datetime localtime show-timezone msec year</br> | ||
| + | 5. ip inspect audit-trail</br> | ||
| + | |||
| + | Commands to enable login/logout logs on Cisco switch.</br> | ||
| + | 1. login on-failure log every 1</br> | ||
| + | 2. login on-success log every 1</br> | ||
| + | |||
| + | == Verifying SYSLOG data collection == | ||
| + | |||
| + | After you enable the syslog forwarding on the end device, you must verify if the logs are being really received by KHIKA Data Aggregator. Please refer [[Getting Data into KHIKA#Verifying syslog data collection|here]] to understand how to verify syslogs on KHIKA Data Aggregator. | ||
| + | |||
| + | == How to Install the KHIKA App for Cisco Switch? == | ||
| + | |||
| + | It is assumed, that you have already configured KHIKA Data Aggregator in your environment. If not, please read [[Getting Started with KHIKA SaaS#Installing and configuring KHIKA Data Aggregator|how to configure KHIKA Data Aggregator]] and perform the pre-requisite steps. | ||
| + | |||
| + | This section explains how to pick and install the KHIKA application for Cisco Switch. Installing the application shall put together and activate the adapter (parser) that can handle Cisco Switch data format, the dashboards, and the alert rules preconfigured. | ||
| + | |||
| + | Go to the “Applications” tab in the “Configure” menu. | ||
| + | |||
| + | [[File:application_index_cisco_switch.jpg|700px]] | ||
| + | |||
| + | Check whether the appropriate Workspace is selected. | ||
| + | Note: Application is always loaded in a Workspace. Read the section [[KHIKA Workspaces|KHIKA Workspaces]] to know more about KHIKA Workspaces. | ||
| + | Also select your KHIKA aggregator name in the Node dropdown. | ||
| + | This is to ensure that we are collecting data from the desired source and into the correct workspace which is ready with the configured application and components. | ||
| + | |||
| + | [[File:cisco_app.jpg|700px]] | ||
| + | |||
| + | Click on the “+” button. A pop up appears. | ||
| + | |||
| + | [[File:cisco_app_popup.jpg|700px]] | ||
| + | |||
| + | User can now select the contents of the application required. For example, on the dropdown for “Reports”, click to expand it. List of all reports can be seen. User can individually select the reports required by checking on the checkbox next to each. Alternatively, check on “Select All” option to get all of them. | ||
| + | Similarly you can select contents from Alerts and Dashboards. | ||
| + | |||
| + | Visit the sections on [[KHIKA Reports| KHIKA Reports]], [[KHIKA Dashboards| KHIKA Dashboards]], [[KHIKA Alerts & Correlations| KHIKA Alerts & Correlations]] to know more about these topics. | ||
| + | |||
| + | Click “OK” to proceed with the installation of the selected Application. | ||
| + | After successful installation, following status should be displayed : | ||
| + | |||
| + | [[File:after_cisco_install.jpg|700px]] | ||
| + | |||
| + | This simple procedure to install a KHIKA App, automatically configures the Adapter (required for parsing the data from raw syslogs), calculated KHIKA reports on raw data, Visualizations, Dashboards and Alerts – all in one click. | ||
| + | |||
| + | == Adding the device in the Adaptor == | ||
| + | After syslogs are enabled on the device and the App is installed into KHIKA, it is the time to add the device to the this App (in Adapter section of KHIKA Web GUI). Please refer [[Getting Data into KHIKA#Adding device details in the Adaptor|here]] to know [[Getting Data into KHIKA#Adding device details in the Adaptor|how to add the device to an App]]. | ||
| + | |||
| + | After making these configurations in KHIKA, you must apply these changes to the Workspace. Go to Configure, select the Workspace and in Workspace tab of configure menu press the Apply button as shown in the screenshot below. | ||
| + | |||
| + | [[File:apply_configuration_cisco.jpg|1100px]] | ||
| + | |||
| + | |||
| + | Wait for a few minutes for changes to apply and data to arrive in kHIKA. With all these steps, we should now expect the data to arrive in KHIKA. Lets discover some live data in KHIKA. | ||
| + | |||
| + | == How to check the output of Cisco Switch App ? == | ||
| + | |||
| + | ===Discovering the logs of Cisco Switch=== | ||
| + | After doing all the steps given above, we should start receiving live data into KHIKA. Go to "Discover" section in KHIKA GUI and select the index with name "*raw-ciscosys*". Note that the index has a prefix of the customer name and workspace name. After selecting this index, you should see the live data coming in. Spend some time understanding this data and the fields of the data. | ||
=== Cisco Router Switch Link Status Dashboard=== | === Cisco Router Switch Link Status Dashboard=== | ||
| Line 14: | Line 86: | ||
|'''Description''' | |'''Description''' | ||
|- | |- | ||
| − | |Contribution of Link Status | + | |Contribution of Link Status |
| − | |Contribution of Link Up/Down status | + | |Contribution of Link Up/Down status on the switch |
|- | |- | ||
| − | |Contribution of Device IP | + | |Contribution of Device IP |
| − | |Contribution of Switches | + | |Contribution of Switches available in the network |
|- | |- | ||
| − | |Interface wise Link Status | + | |Interface wise Link Status |
| − | |X axis : | + | |X axis : "Interfaces" which are present in Cisco switch <br/> |
| − | Y axis : stacked | + | Y axis : stacked of the status of link and count of events occurred. |
|- | |- | ||
| − | |Contribution of Facility and Severity | + | |Contribution of Facility and Severity |
| − | |X axis : | + | |X axis : "Facilities" which are available in switch<br/> |
| − | Y axis : stacked | + | Y axis : stacked of Severity like information, error, notification, etc. and count of events occurred. |
|- | |- | ||
| − | | | + | |Daily Trend |
|Trend of events over time. Useful to identify unusual spikes at a glance.<br/><br/>X axis : date & time<br/>Y axis : count of events | |Trend of events over time. Useful to identify unusual spikes at a glance.<br/><br/>X axis : date & time<br/>Y axis : count of events | ||
|- | |- | ||
| Line 38: | Line 110: | ||
==== Suggestion for useful interaction with this dashboard could be : ==== | ==== Suggestion for useful interaction with this dashboard could be : ==== | ||
| − | #Click on | + | #Click on "Down" from status field in "Contribution of Link Status" pie chart. This gets selected and a filter for selected downstate is applied across the rest of the dashboard. The next pie chart shall show the "switches" which are in downstate.The next bar chart shall show "Interfaces" which are in the down state. Details about selected down status can be seen in the summary table. How to remove this filter is explained [[Filter information on Dashboards|here]] |
=== Cisco Switch Login Activity Dashboard === | === Cisco Switch Login Activity Dashboard === | ||
| Line 54: | Line 126: | ||
|'''Description''' | |'''Description''' | ||
|- | |- | ||
| − | + | |Contribution of Login Status | |
| − | |||
| − | |||
| − | |Contribution of Login Status | ||
|Contribution of success/failed status. | |Contribution of success/failed status. | ||
|- | |- | ||
| − | |Contribution of Users | + | |Contribution of Users |
|Contribution of Users which are logged in. | |Contribution of Users which are logged in. | ||
| − | |Source wise Local Port | + | |- |
| + | |Source wise Local Port | ||
|X axis : Source IP where users are logged in<br/> | |X axis : Source IP where users are logged in<br/> | ||
| − | Y axis : stacked | + | Y axis : stacked of Local port and count of events occurred. |
|- | |- | ||
|Daily Trend | |Daily Trend | ||
| Line 76: | Line 146: | ||
==== A suggestion for useful interaction with this dashboard could be : ==== | ==== A suggestion for useful interaction with this dashboard could be : ==== | ||
| − | #Examine the time trend, for a higher number of events. Rest of the dashboard also gets filtered and we can isolate all the Users and status of executed action in a pie chart. In the next bar chart, we can isolate Source IP where users can | + | #Examine the time trend, for a higher number of events. Rest of the dashboard also gets filtered and we can isolate all the Users and status of executed action in a pie chart. In the next bar chart, we can isolate Source IP where users can logged in and also port which is used for logged in. Details of all activities in the selected time range can be seen in the summary table. |
| − | #Click on a particular | + | #Click on a particular "User" from "Contribution of Users" pie chart, Rest of the dashboard gets filtered and we can isolate login status, IP address of selected user port information which is used for logging and all the detailed information of the selected user in "Summary Table" |
| − | |||
=== Severity Report Dashboard === | === Severity Report Dashboard === | ||
Go to "Dashboards" from the left menu. From the list of in-built dashboards, select this one. It shall open the Dashboard. This dashboard focuses on | Go to "Dashboards" from the left menu. From the list of in-built dashboards, select this one. It shall open the Dashboard. This dashboard focuses on | ||
| − | the Severity of Events. Details like which Events | + | the Severity of Events. Details like which Events are generated and what is their severity can be seen. Also, messages available in the event, Device IP, etc. are shown in an analytical fashion. |
You can filter and search for information and create new ones too. For help with Dashboards, click [[KHIKA Dashboards|here]] | You can filter and search for information and create new ones too. For help with Dashboards, click [[KHIKA Dashboards|here]] | ||
| Line 98: | Line 167: | ||
|Events wise Messages | |Events wise Messages | ||
|X axis : "Information" about generated events on switch<br/> | |X axis : "Information" about generated events on switch<br/> | ||
| − | Y axis : stacked | + | Y axis : stacked of the message available in each event and count of events occurred. |
|- | |- | ||
| − | |Contribution of Severity | + | |Contribution of Severity |
|Contribution of Severity level like information, error, warning, etc. | |Contribution of Severity level like information, error, warning, etc. | ||
|- | |- | ||
|Contribution of Facility and Severity | |Contribution of Facility and Severity | ||
| − | |X axis : " | + | |X axis : "Facilities" available on switch<br/> |
| − | Y Axis : stacked | + | Y Axis : stacked of the Severity for each specific facility on switch |
|- | |- | ||
| − | | | + | |Daily Trend |
|Trend of events over time. Useful to identify unusual spikes at a glance.<br/><br/>X axis : date & time<br/>Y axis : count of events | |Trend of events over time. Useful to identify unusual spikes at a glance.<br/><br/>X axis : date & time<br/>Y axis : count of events | ||
|- | |- | ||
| Line 114: | Line 183: | ||
|} | |} | ||
| − | |||
==== Some suggestions for useful interaction with this dashboard could be : ==== | ==== Some suggestions for useful interaction with this dashboard could be : ==== | ||
| − | #Click on "error" severity in the “Contribution of Severity” pie chart. The rest of the dashboard gets filtered and shows only | + | #Click on "error" severity in the “Contribution of Severity” pie chart. The rest of the dashboard gets filtered and shows only detailed information about selected "error" severity events. So we can isolate - information of all the events which have error severity, available in events wise messages bar chart. Also in "Contribution of Facility and Severity" charts we can see various facilities which have the error severity. |
=== System Information Report Dashboard === | === System Information Report Dashboard === | ||
| − | Go to "Dashboards" from the left menu. From the list of in-built dashboards, select this one. It shall open the Dashboard. This dashboard focused on System Information Report details. | + | Go to "Dashboards" from the left menu. From the list of in-built dashboards, select this one. It shall open the Dashboard. This dashboard focused on System Information Report details. It shows changes in the configuration on the system , Severity of events and Device IP of switches available in the network, etc. |
You can filter and search for information and create new ones too. For help with Dashboards, click [[KHIKA Dashboards|here]] | You can filter and search for information and create new ones too. For help with Dashboards, click [[KHIKA Dashboards|here]] | ||
| Line 134: | Line 202: | ||
|'''Description''' | |'''Description''' | ||
|- | |- | ||
| − | |Contribution of System Activities | + | |Contribution of System Activities |
|contribution of activities on the switch as configuration changed, login events, etc | |contribution of activities on the switch as configuration changed, login events, etc | ||
|- | |- | ||
| Line 142: | Line 210: | ||
|- | |- | ||
|Contribution of Severity | |Contribution of Severity | ||
| − | |contribution of information | + | |contribution of severity like information, notification has occurred and its count. |
|- | |- | ||
| − | | | + | |Daily Trend |
|Trend of events over time. Useful to identify unusual spikes at a glance.<br/><br/>X axis : date & time<br/>Y axis : count of events | |Trend of events over time. Useful to identify unusual spikes at a glance.<br/><br/>X axis : date & time<br/>Y axis : count of events | ||
|- | |- | ||
| Line 150: | Line 218: | ||
|Detailed data with timestamp and count | |Detailed data with timestamp and count | ||
|} | |} | ||
| − | |||
==== Some suggestions for useful interaction with this dashboard could be : ==== | ==== Some suggestions for useful interaction with this dashboard could be : ==== | ||
| − | #Click on a particular Device IP in the “Device IP wise Information” bar chart. You can monitor all the activities of this device, it isolates the severity level of the message and also configuration and logging information. Detailed information | + | #Click on a particular "Device IP" in the “Device IP wise Information” bar chart. You can monitor all the activities of this device, it isolates the severity level of the message and also configuration and logging information. Detailed information can be seen for the selected device in "Summary Table" |
| − | |||
| − | |||
| − | |||
| + | === Cisco Switch Alerts === | ||
| − | |||
| − | |||
| − | + | Alerts are generated when certain critical behavior is observed in the system. Alerts can be monitored in real-time on the Alerts Dashboard in KHIKA. Relevant stakeholders can also receive the alerts via emails. The table below explains all the pre-canned alerts shipped with KHIKA App for Cisco Switch. | |
==== Alerts Description ==== | ==== Alerts Description ==== | ||
| Line 194: | Line 257: | ||
|- | |- | ||
|Link down on switch | |Link down on switch | ||
| − | |This alert is triggered when "changed state to down" message available in an event for particular switch device. | + | |This alert is triggered when "changed state to down" message available in an event for a particular switch device. |
|Link down on switch <br/><br/> | |Link down on switch <br/><br/> | ||
Admin may refer switch manual to take required action.<br/><br/> | Admin may refer switch manual to take required action.<br/><br/> | ||
|} | |} | ||
Latest revision as of 00:50, 31 March 2020
Contents
- 1 Introduction
- 2 Enabling Syslog forwarding on the device
- 3 Verifying SYSLOG data collection
- 4 How to Install the KHIKA App for Cisco Switch?
- 5 Adding the device in the Adaptor
- 6 How to check the output of Cisco Switch App ?
Introduction
Most of the network devices, such as firewalls, switches, routers, web proxies etc send the traffic and user activity related information in the form of logs over syslog protocol. Some applications such as Oracle database server, Symantec antivirus server, EMC SAN Storage etc also support syslog protocol as syslog is very efficient and simple to integrate with. KHIKA Data Aggregator is pre-configured with syslog services on port 514. The key parts to get here are :
- Enabling Syslog forwarding on the device
- Install the KHIKA App for Cisco Switch
- Get data from your Cisco Switch into KHIKA Aggregator
Enabling Syslog forwarding on the device
Please refer "Configuring the UNIX System Logging Facility" section in Cisco Switch Documentation for enabling syslogs on your cisco switch device.
Example of commands to be fired on Cisco Switch Device to enable syslogs:
1. logging <IP Address of khika aggregator>
2. logging trap debugging (7)
3. logging on
4. service timestamps log datetime localtime show-timezone msec year
5. ip inspect audit-trail
Commands to enable login/logout logs on Cisco switch.
1. login on-failure log every 1
2. login on-success log every 1
Verifying SYSLOG data collection
After you enable the syslog forwarding on the end device, you must verify if the logs are being really received by KHIKA Data Aggregator. Please refer here to understand how to verify syslogs on KHIKA Data Aggregator.
How to Install the KHIKA App for Cisco Switch?
It is assumed, that you have already configured KHIKA Data Aggregator in your environment. If not, please read how to configure KHIKA Data Aggregator and perform the pre-requisite steps.
This section explains how to pick and install the KHIKA application for Cisco Switch. Installing the application shall put together and activate the adapter (parser) that can handle Cisco Switch data format, the dashboards, and the alert rules preconfigured.
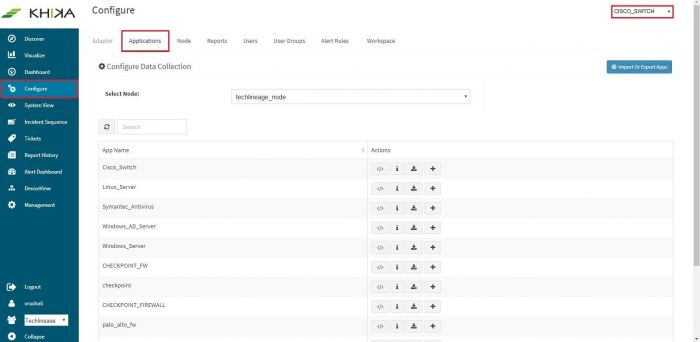
Go to the “Applications” tab in the “Configure” menu.
Check whether the appropriate Workspace is selected. Note: Application is always loaded in a Workspace. Read the section KHIKA Workspaces to know more about KHIKA Workspaces. Also select your KHIKA aggregator name in the Node dropdown. This is to ensure that we are collecting data from the desired source and into the correct workspace which is ready with the configured application and components.
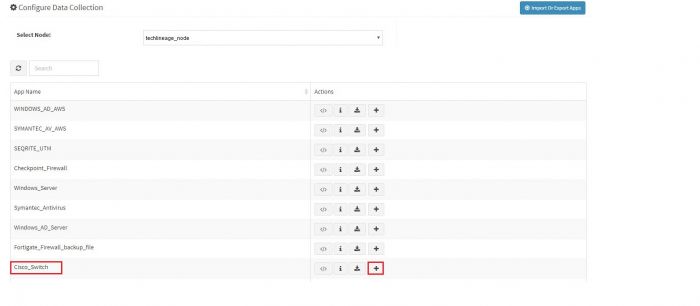
Click on the “+” button. A pop up appears.
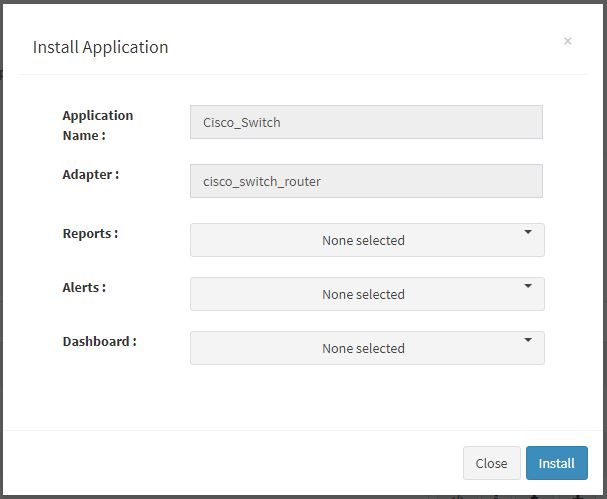
User can now select the contents of the application required. For example, on the dropdown for “Reports”, click to expand it. List of all reports can be seen. User can individually select the reports required by checking on the checkbox next to each. Alternatively, check on “Select All” option to get all of them. Similarly you can select contents from Alerts and Dashboards.
Visit the sections on KHIKA Reports, KHIKA Dashboards, KHIKA Alerts & Correlations to know more about these topics.
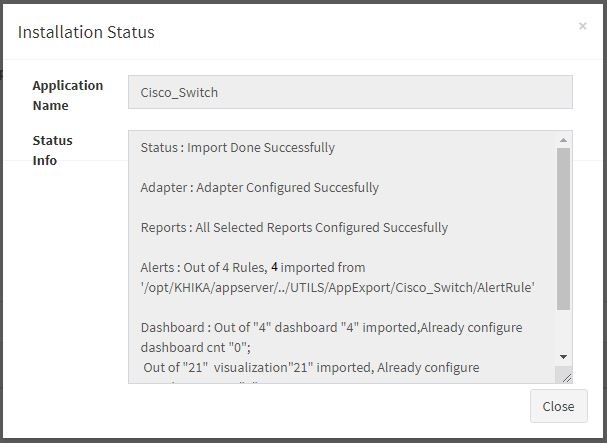
Click “OK” to proceed with the installation of the selected Application. After successful installation, following status should be displayed :
This simple procedure to install a KHIKA App, automatically configures the Adapter (required for parsing the data from raw syslogs), calculated KHIKA reports on raw data, Visualizations, Dashboards and Alerts – all in one click.
Adding the device in the Adaptor
After syslogs are enabled on the device and the App is installed into KHIKA, it is the time to add the device to the this App (in Adapter section of KHIKA Web GUI). Please refer here to know how to add the device to an App.
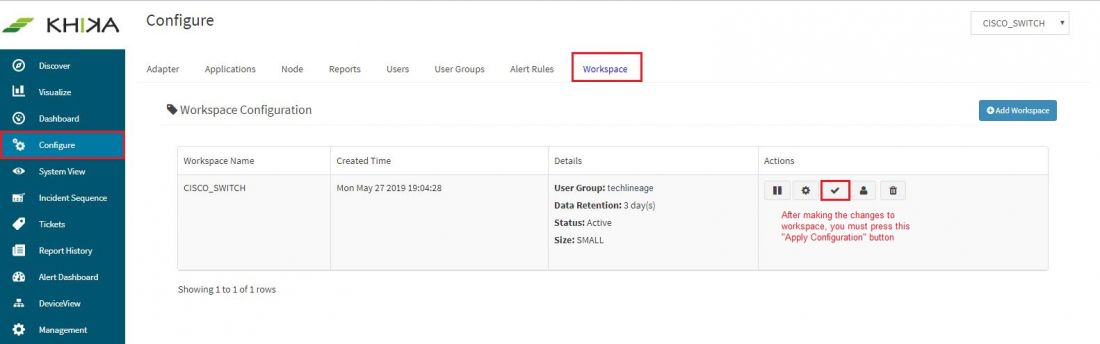
After making these configurations in KHIKA, you must apply these changes to the Workspace. Go to Configure, select the Workspace and in Workspace tab of configure menu press the Apply button as shown in the screenshot below.
Wait for a few minutes for changes to apply and data to arrive in kHIKA. With all these steps, we should now expect the data to arrive in KHIKA. Lets discover some live data in KHIKA.
How to check the output of Cisco Switch App ?
Discovering the logs of Cisco Switch
After doing all the steps given above, we should start receiving live data into KHIKA. Go to "Discover" section in KHIKA GUI and select the index with name "*raw-ciscosys*". Note that the index has a prefix of the customer name and workspace name. After selecting this index, you should see the live data coming in. Spend some time understanding this data and the fields of the data.
Cisco Router Switch Link Status Dashboard
Go to "Dashboards" from the left menu. From the list of in-built dashboards, select this one. It shall open the Dashboard. This dashboard focuses on the Link status of Cisco Switch(which are added into KHIKA). Details like the link is Up or Down, available interfaces on the switch are shown in an analytical fashion. You can filter and search for information and create new ones too. For help with Dashboards, click here
Elements in the Dashboard are explained below :
| Visualization | Description |
| Contribution of Link Status | Contribution of Link Up/Down status on the switch |
| Contribution of Device IP | Contribution of Switches available in the network |
| Interface wise Link Status | X axis : "Interfaces" which are present in Cisco switch Y axis : stacked of the status of link and count of events occurred. |
| Contribution of Facility and Severity | X axis : "Facilities" which are available in switch Y axis : stacked of Severity like information, error, notification, etc. and count of events occurred. |
| Daily Trend | Trend of events over time. Useful to identify unusual spikes at a glance. X axis : date & time Y axis : count of events |
| Summary Table | Detailed data with timestamp and count |
Suggestion for useful interaction with this dashboard could be :
- Click on "Down" from status field in "Contribution of Link Status" pie chart. This gets selected and a filter for selected downstate is applied across the rest of the dashboard. The next pie chart shall show the "switches" which are in downstate.The next bar chart shall show "Interfaces" which are in the down state. Details about selected down status can be seen in the summary table. How to remove this filter is explained here
Cisco Switch Login Activity Dashboard
Go to "Dashboards" from the left menu. From the list of in-built dashboards, select this one. It shall open the Dashboard.This dashboard focuses on the login activity of users in Cisco Switch. Details like which user logged in how many times, login status, authentication information, Configuration changes, etc. is shown in an analytical fashion. You can filter and search for information and create new ones too. For help with Dashboards, click here
Elements in the Dashboard are explained below :
| Visualization | Description |
| Contribution of Login Status | Contribution of success/failed status. |
| Contribution of Users | Contribution of Users which are logged in. |
| Source wise Local Port | X axis : Source IP where users are logged in Y axis : stacked of Local port and count of events occurred. |
| Daily Trend | Trend of login events over time. Useful to identify unusual spikes at a glance. X axis : date & time Y axis : count of events |
| Summary Table | Detailed data with timestamp and count |
A suggestion for useful interaction with this dashboard could be :
- Examine the time trend, for a higher number of events. Rest of the dashboard also gets filtered and we can isolate all the Users and status of executed action in a pie chart. In the next bar chart, we can isolate Source IP where users can logged in and also port which is used for logged in. Details of all activities in the selected time range can be seen in the summary table.
- Click on a particular "User" from "Contribution of Users" pie chart, Rest of the dashboard gets filtered and we can isolate login status, IP address of selected user port information which is used for logging and all the detailed information of the selected user in "Summary Table"
Severity Report Dashboard
Go to "Dashboards" from the left menu. From the list of in-built dashboards, select this one. It shall open the Dashboard. This dashboard focuses on the Severity of Events. Details like which Events are generated and what is their severity can be seen. Also, messages available in the event, Device IP, etc. are shown in an analytical fashion.
You can filter and search for information and create new ones too. For help with Dashboards, click here
Elements in the Dashboard are explained below :
| Visualization | Description |
| Events wise Messages | X axis : "Information" about generated events on switch Y axis : stacked of the message available in each event and count of events occurred. |
| Contribution of Severity | Contribution of Severity level like information, error, warning, etc. |
| Contribution of Facility and Severity | X axis : "Facilities" available on switch Y Axis : stacked of the Severity for each specific facility on switch |
| Daily Trend | Trend of events over time. Useful to identify unusual spikes at a glance. X axis : date & time Y axis : count of events |
| Summary Table | Detailed data with timestamp and count |
Some suggestions for useful interaction with this dashboard could be :
- Click on "error" severity in the “Contribution of Severity” pie chart. The rest of the dashboard gets filtered and shows only detailed information about selected "error" severity events. So we can isolate - information of all the events which have error severity, available in events wise messages bar chart. Also in "Contribution of Facility and Severity" charts we can see various facilities which have the error severity.
System Information Report Dashboard
Go to "Dashboards" from the left menu. From the list of in-built dashboards, select this one. It shall open the Dashboard. This dashboard focused on System Information Report details. It shows changes in the configuration on the system , Severity of events and Device IP of switches available in the network, etc.
You can filter and search for information and create new ones too. For help with Dashboards, click here
Elements in the Dashboard are explained below :
| Visualization | Description |
| Contribution of System Activities | contribution of activities on the switch as configuration changed, login events, etc |
| Device IP wise Information | X axis : "Information" of event Y axis : Device IP of switch available in network.count of events occurred on the device. |
| Contribution of Severity | contribution of severity like information, notification has occurred and its count. |
| Daily Trend | Trend of events over time. Useful to identify unusual spikes at a glance. X axis : date & time Y axis : count of events |
| Summary Table | Detailed data with timestamp and count |
Some suggestions for useful interaction with this dashboard could be :
- Click on a particular "Device IP" in the “Device IP wise Information” bar chart. You can monitor all the activities of this device, it isolates the severity level of the message and also configuration and logging information. Detailed information can be seen for the selected device in "Summary Table"
Cisco Switch Alerts
Alerts are generated when certain critical behavior is observed in the system. Alerts can be monitored in real-time on the Alerts Dashboard in KHIKA. Relevant stakeholders can also receive the alerts via emails. The table below explains all the pre-canned alerts shipped with KHIKA App for Cisco Switch.
Alerts Description
| Alert Name | Description | Suggested Resolution |
| Neighbor Down of a Switch | This alert is triggered when the event occurs such that a neighbor is in the down state. | This alert signifies that the neighbor relationship with the corresponding router/switch is down. This typically happens when Router/Switch does not receive keepalive/HELLO packets from the neighbor for a period of time longer than the Dead timer interval. If neighbor in the downstate, verify that the neighbor router is up, is running, and is properly configured for OSPF on the interface. You may refer the OEM Router/Switch manual for further information in this regard. |
| Command executed on switch | This alert is triggered when "cfglog_loggedcmd" message is available in the event. | Certain Commands have been executed on switch. You need to ensure that admin/configuration change commands are executed by authorized user only. |
| SLA Down on a Switch | This alert is triggered when the state changed Up to Down for SLA reachability | With Cisco IOS IP SLAs, service provider customers can measure and provide. service level agreements, and enterprise customers can verify service levels, verify outsourced service level agreements, and understand network performance. Cisco IOS IP SLAs can perform network assessments, verify quality of service (QoS), ease the deployment of new services, and assist with network troubleshooting. This alert denotes that network performance (as defined by SLAs) between multiple network locations or across multiple network paths is down/lower than expected SLAs. |
| Link down on switch | This alert is triggered when "changed state to down" message available in an event for a particular switch device. | Link down on switch Admin may refer switch manual to take required action. |